Emotet kill switch: Exploiting the exploiters
At the end of July we reported how Emotet was making a…
IoT Security – Why is it Important?
IoT or Internet of Things are connected devices, including hardware, software and…
Not the WordPress Newsletter you’ll want to receive
Wordpress is by far the most popular CMS out there, but it's…
Threat Intelligence Automation
Cyber Threat Intelligence (CTI) is a framework and technology that generates intelligence…
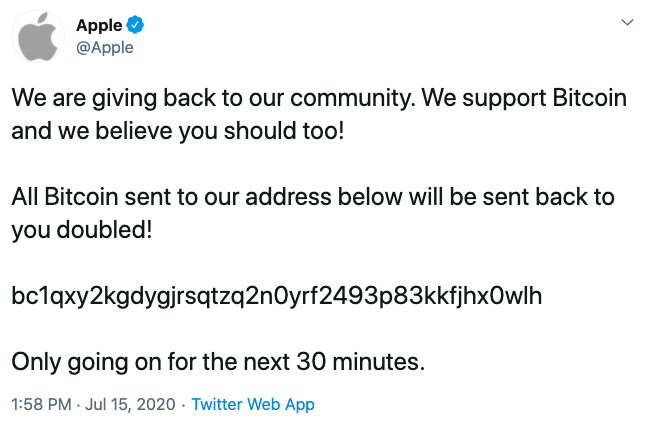
Twitter Hack Meltdown: phishing is the culprit
The Twitter hack meltdown that happened a few week ago which has…
Dell PowerEdge Server, trouble on the horizion?
Crisis averted for Dell PowerEdge servers, after a group of researchers disclosed…
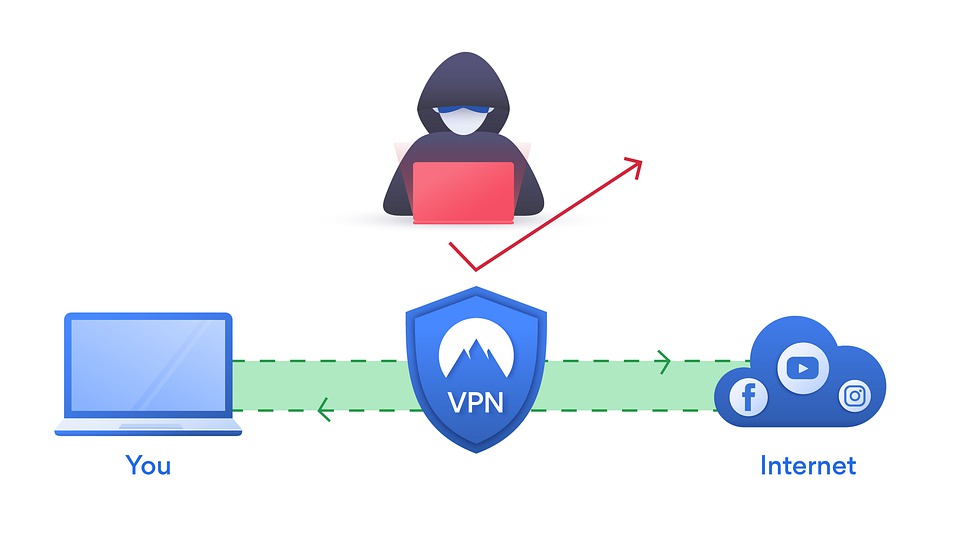
VPN users beware, this flaw could compromise your entire infrastructure
VPN have been one of the "stars" of this pandemic era. Office…
OWASP – Open Web Application Security Project
The Open Web Application Security Project (OWASP) has compiled a list of…
Emotet is back, but how do we know if we are being targeted?
After a break of five months Emotet is back with a vengeance…