Latest News By Security Parrot
OpenAI may use Associated Press archive for AI training
OpenAI and Associated Press Partner Up to Utilize Generative AI OpenAI has been granted access…
EU users can hold conversations with Google Bard from training set
Google's Chatbot Bard Now Available in Europe with Privacy Hub Google released its chatbot Bard…
EXPERT INSIGHTS
28 dangerous extensions detected for Google Chrome and Microsoft Edge
Avast experts have discovered malware hidden in at least 28 third-party extensions for Google Chrome and Microsoft Edge. All of these extensions were…
Tuttorials
Metasploit with Docker and Kubernetes
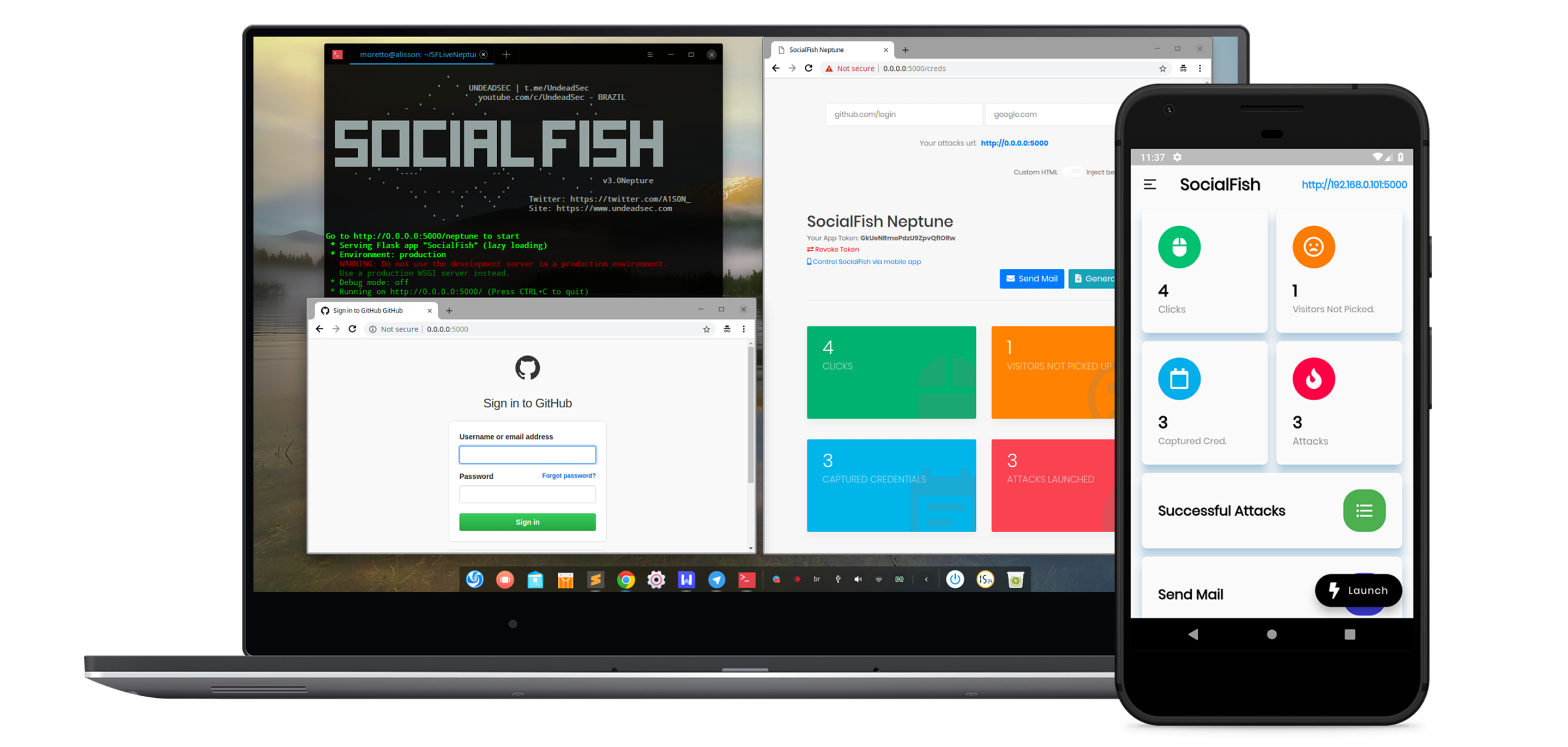
SocialFish – Let’s Go Phishing
Always Stay Up to Date
Subscribe to our newsletter to get our newest articles instantly!
Read More
AVrecon Botnet Infects Over 70,000 Linux Routers
AVrecon Linux Malware Infects Over 70,000 SOHO Routers Since May 2021, the AVrecon Linux malware has infected more than 70,000 SOHO routers and made most…
Twitter creates revenue model for verified creators
Twitter Launches Revenue Model for Creators Twitter has announced a new revenue model for creators on the platform, allowing them to share in the ad…
WordPress security plugin AIOS stored passwords as plain text
AIOS WordPress Security Plugin Collects Passwords and Stores Them as Plain Text WordPress security plugin All-In-One Security (AIOS) has been found to do the exact…
Google Play is going to tackle malicious apps with DUNS number
Google Play to Make it Harder to Upload Malicious Apps Google Play will make it more difficult to upload malicious apps to its app store…
Microsoft releases more Rust features for Windows kernel
Microsoft Releases New Features for Windows' Rust Kernel in Latest Insider Build Microsoft has been working on initiatives around the Rust programming language for a…
Meta’s VP metaverse is optimistic: ‘The metaverse hype is dead’
Metaverse Hype is Dead, But the Time is Now Ripe to Build the Digital World The metaverse hype is dead, according to Vishal Shah, vice…
Statcounter: 3% of all desktops in the world are running Linux
Linux Distribution Reaches Record 3.07% Share in Global Desktop Operating System Market Analysts at Statcounter have calculated that the share of Linux distributions in the…
ACS through the eyes of a hacker. Attacking RFID Access Control Systems
Exploring the Security Vulnerabilities of EM4100 RFID-Based Access Control Systems Hacking electronic turnstiles at the entrance to the building is a cherished hacker flex that…
Cisco koopt Identity Threat Detection and Response-startup Oort
Cisco Acquires Identity Threat Detection and Response Startup Oort Cisco has announced its acquisition of Identity Threat Detection and Response (ITDR) startup Oort. The technology…
Oracle introduces Race Data Experience Center in Utrecht
Oracle Opens Race Data Experience Center in Utrecht to Showcase Cloud Infrastructure Oracle has announced the opening of a Race Data Experience Center in Utrecht,…
Windows 11 23H2 will be released in the fourth quarter
Microsoft Announces Windows 11 23H2 Update Microsoft has announced the upcoming Windows 11 major update, set to be released in the fourth quarter of this…
Podcast: Information security in the banking sector – from ‘one-man show’ to (international) cooperation
Cybersecurity in the Banking World: A Conversation with Michael Samson The Early Days of Information Security In few sectors will the subject of cybersecurity receive…
Chinese email hack only detectable with the most expensive Microsoft subscription
Biden Administration Questions Microsoft's Cloud Computing Services The Biden administration is questioning Microsoft's cloud computing services after the Chinese email hack was discovered. The tech…
How an agile data platform leads to much more than CSRD compliance
CSRD: Achieving Compliance and Maximum ESG Value Many companies are now investing in environmental, social & governance (ESG) because they understand that this affects business…
GitHub will support passwordless authentication with passkeys
GitHub Now Supports Passwordless Authentication in Public Beta GitHub Introduces Passwordless Authentication Developer platform GitHub now supports passwordless authentication in a public beta. This allows…
AVrecon: The malware with a botnet army of tens of thousands of routers
AVrecon: The Malware That Has Been Flying Under the Radar for Two Years Researchers at Black Lotus Labs have recently discovered a malware variant that…
Information security specialist accused of hacking a cryptocurrency exchange and stealing $9 million
Cybersecurity Specialist Arrested for Stealing $9 Million from Cryptocurrency Exchange U.S. authorities have announced the arrest of cybersecurity specialist Shakeeb Ahmed, who is accused of…
Azure AD becomes Entra: Microsoft is acting like an elephant in the china shop
Microsoft Renames Azure AD to Microsoft Entra ID Microsoft is bringing its identity and access management tool, Azure Active Directory (AD), into its Identity and…
Ransomware activity is breaking records. In June, they asked the victims for 449.1 million dollars
Ransomware Attacks on the Rise in 2023 Ransomware Revenues on the Rise According to a report from Chainalysis, ransomware is the only cybercriminal activity that…
Russian Hackers Attack Western Diplomats Through BMW Sale Advertisement
APT29 Hackers Use Unusual Baits to Target Diplomats in Ukraine The Russian-speaking hack group APT29 (aka Nobelium and Cloaked Ursa) has been using unusual baits…