The Twitter hack meltdown that happened a few week ago which has made the news everywhere and involved the profiles of celebrities and politicians alike has finally been unraveled.
Apparently the initial “in” for the Criminal Hacker was a mobile spearfishing attack targeting a small number of employees.
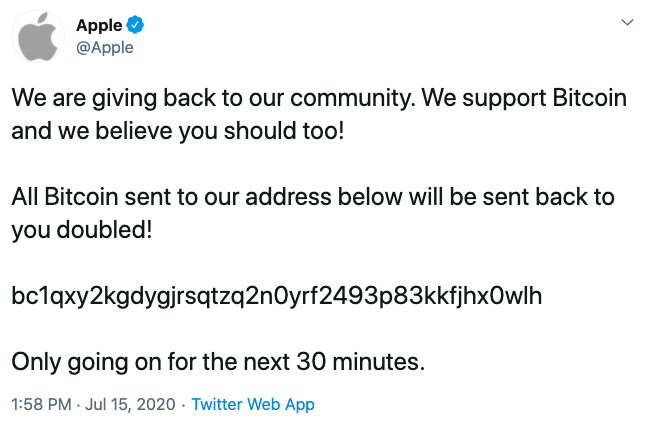
The takeover of these account was all in the name of pushing out a Bitcoin scam, which allegedly netted over 100 thousand dollars.
Twitter, to clarify the situation, posted a blog on the incident.
“The social engineering that occurred on July 15, 2020, targeted a small number of employees through a phone spear phishing attack. A successful attack required the attackers to obtain access to both our internal network as well as specific employee credentials that granted them access to our internal support tools“, the company admitted.
“Not all of the employees that were initially targeted had permissions to use account management tools, but the attackers used their credentials to access our internal systems and gain information about our processes. This knowledge then enabled them to target additional employees who did have access to our account support tools. Using the credentials of employees with access to these tools, the attackers targeted 130 Twitter accounts, ultimately Tweeting from 45, accessing the DM inbox of 36, and downloading the Twitter Data of 7″.
In short a full blown account takeover and compromise of some of their employees…
What has been done
Since the attack Twitter has said that “we’ve significantly limited access to our internal tools and systems to ensure ongoing account security while we complete our investigation. As a result, some features (namely, accessing the Your Twitter Data download feature) and processes have been impacted”.
On top of that, the company has admitted that the cyber attack has somewhat affected its ability to respond to customer support needs and to other various issues like “reported Tweets, and applications to our developer platform”.
All of this in the name of making durable changes to their processes and tooling as a result of the incident.
Twitter is promising an increase in it’s security protocols, techniques and mechanisms. “it’s how we work to stay ahead of threats as they evolve”, they said.
Twitter Hack: Better late than never
One of the measures implemented will be a company wide Cyber awareness training course, with a particoular focus on phishing and other social engineering scams.
“We will continue to share updates and precautionary steps we take so that others can learn from this, too. We recognize the trust you place in us, and are committing to earning it by continued open, honest and timely updates anytime an incident like this happens”.
So, in short, “we are licking our wounds we will behave form now on”.