Network Vulnerability Assessment ? Why Should Every Company Do it at least once a Year !
Network vulnerability assessment analyzes a variety of network issues, prioritizes the most…
Cisco Network Security may be compromised by this flaw
Cisco has just warned that a high-severity flaw in its network security…
Oops! Lazarus back at it with a new Multi-Platform Malware Framework
Windows, Linux, and even macOS operating systems, seems like nobody is safe…
Machine Learning in Malware Analysis
Many different deep network architectures have been suggested by machine learning experts…
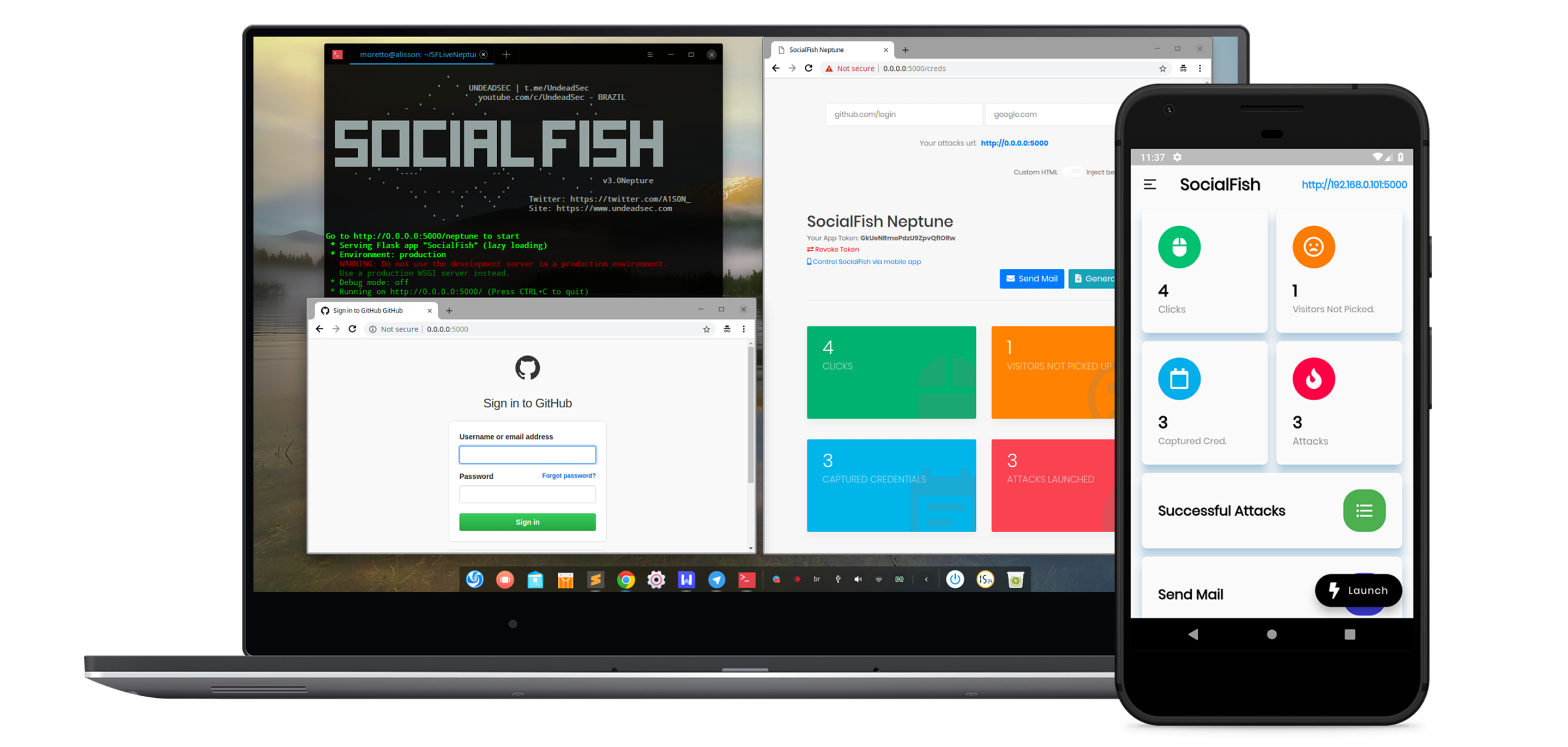
SocialFish – Let’s Go Phishing
SocialFish is an open-source phishing tool, integrated with another open source tool…
Automation Of Penetration Testing With Machine Learning
Penetration Testing in Simple Words, is to identify and indicate a vulnerability…
Astsu – A network scanner tool
A network scanner tool, developed in Python 3 using scapy. How it…
Elasticsearch Data Breach – Genealogy Software Maker Exposes Data on 60,000 Users
A US tech company that manages popular family tree software has exposed…
Artificial Intelligence and Cyber Security
As artificial intelligence intrudes into the world of cybersecurity, security analysts and…
Emotet Botnet is Back!
Emotet, one of today's most prominent malware botnets, has come back to…