Microsoft experts said that attackers could use a macOS vulnerability to bypass Transparency, Consent, and Control (TCC) technology and gain access to protected user data.
Back in the summer of 2021, a research group informed Apple developers about a vulnerability dubbed powerdir ( CVE-2021-30970 ). The bug is related to the TCC technology, which is designed to block applications from accessing sensitive user data. This allows macOS users to customize privacy settings for apps and devices connected to their Macs, including cameras and microphones.
While Apple has restricted access to TCC (only for apps with full disk access) and configured features to automatically block unauthorized code execution, Microsoft researchers have found that attackers could inject a second custom-built TCC database into the system, allowing them to gain access to a secure information.
The point is that TCC supports two types of databases – one for permissions that apply to a specific user profile, and the other for permissions that apply globally, system-wide, protected by System Integrity Protection (SIP) and are only available for applications with full disk access.
We found that it was possible to programmatically change the target user’s home directory and inject a fake TCC database that stores the history of consent for application requests,” say the experts. – If this vulnerability is exploited, an attacker, in theory, can launch an attack based on the user’s protected personal data. For example, an attacker can hack an application installed on a device (or install his own malicious application), gaining access to a microphone to record private conversations or take screenshots of sensitive information displayed on the screen.
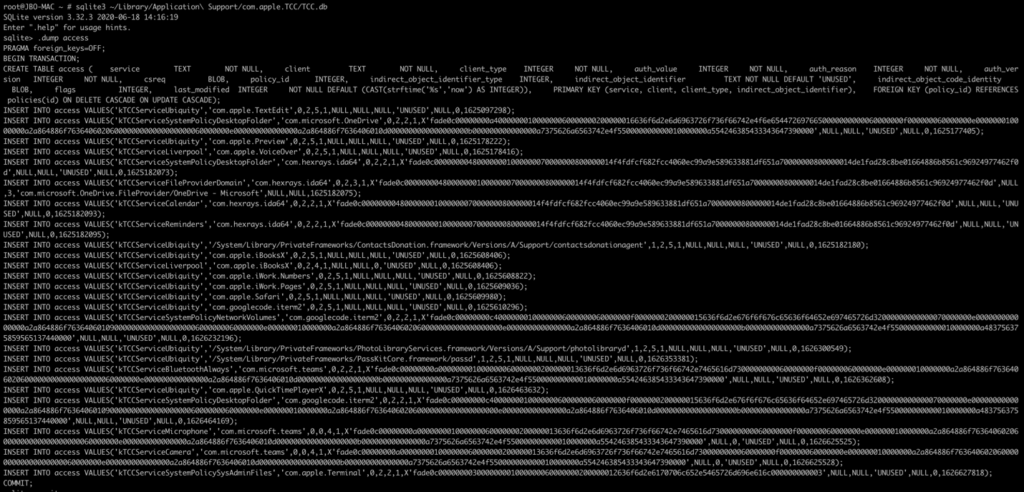
In fact, a user with full disk access can find the TCC.db file, which is a SQLITE database, view it, and even edit it. Thus, an attacker with full access to the TCC databases can grant arbitrary permissions to his malicious applications, which the user will not even know about.
Apple fixed this issue in December 2021 with the release of macOS 11.6 and 12.1.
CVE-2021-30970 is the third TCC bypass issue. Earlier in 2021, Apple fixed bugs CVE-2020-9934 and CVE-2020-27937 , as well as the zero-day vulnerability CVE-2021-30713 , which also allowed an attacker to gain full access to the disk, record data from the screen, and perform other actions without explicit user consent.





