Over the past 16 months, unknown attackers have infiltrated malicious servers into the Tor network, and then used them to intercept cryptocurrency-related traffic and perform SSL stripping attacks.
This campaign started back in January 2020, and its essence was to add to the Tor network the servers, which were marked as exit nodes (that is, the servers through which traffic leaves the Tor network and re-enters the public Internet).
Since then, attackers have injected thousands of malicious servers into the Tor network, and with their help they identified traffic directed to the sites of cryptocurrency mixers, and then launched attacks such as SSL stripping, that is, they downgraded user traffic from HTTPS addresses to less secure HTTP. After downgrading to HTTP, criminals are able to change the addresses of cryptocurrency wallets with their own and intercept transactions.
The attacks were first documented in August last year by an information security specialist and Tor server operator, known under the pseudonym Nusenu. At the time, he reported that on better days, attackers managed to control 23.95% of all Tor exit nodes.
Now Nusenu has published a new study in which he writes that although what is happening has long been publicized, attackers are still continuing their attacks. Even worse, attacks only intensified: in February 2021, criminals even broke their own “record” and were responsible for 27% of all Tor exit nodes.
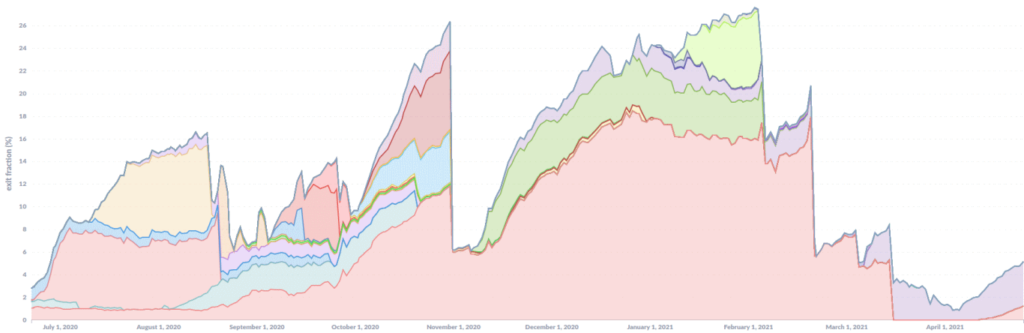
Although the second wave of attacks was eventually discovered and the malicious servers removed from the Tor network, the attackers’ infrastructure had been up and running for weeks or even months before that. The fact is that hackers injected their servers into the network in small portions, accumulating powerful infrastructure and not attracting attention.
This tactic was changed by the hackers only this month: when their infrastructure was turned off again, they tried to restore all the servers at the same time. This attack was detected within 24 hours, because the simultaneous increase in the number of exit nodes from 1500 to 2500 could not be overlooked.
Although more than 1,000 servers are now down, the expert writes that as of May 5, 2021, attackers still control 4% to 6% of Tor exit nodes, and SSL stripping attacks continue.