The creator of Have I Been Pwned, Troy Hunt, uses the domains of Coinhive, a cryptojacking service that was closed in 2019, to alert users to sites that are still mining hidden.
Let me remind you that Coinhive appeared in the fall of 2017 and was then positioned as an alternative to classic banner advertising. As a result, Coinhive only spawned a large-scale phenomenon that information security specialists called cryptojacking, or browser mining. It became enough for users to “unsuccessfully” go to any site, into the code of which a special JavaScript Coinhive (or other similar service, of which there were dozens soon appeared ) is embedded , and the resources of the victims’ machines were already used to extract the Monero cryptocurrency. Although the Coinhive operators admitted that they did not want to create a tool for enriching cybercriminals at all and directly condemned the actions of the cybercriminals.
At its peak, Coinhive has been embedded in 200,000 routers, browser extensions, Microsoft Store apps, and even government websites.
However, in the end, in the spring of 2019, the service closed a year after the Monero hard fork, as the hash rate fell by more than 50%. In addition, the decision of the Coinhive developers was influenced by the general “collapse” of the cryptocurrency market, since then XMR lost about 85% of its value.
As the founder of the leak aggregator Have I Been Pwned (HIBP) Troy Hunt now says in a blog post , he was given access to coinhive.com and other related domains for free, provided he did something useful with them:
“In May 2020, I gained control of both the primary domain coinhive.com and several other secondary domains associated with the service, such as cnhv.co, which was used to shorten links (which also forced browsers to mine Monero).
I’m not sure how much the person who provided me with these domains wants publicity, so the only thing I’ll say now is that they were provided to me for free to do something useful. “
Since the domains are hosted behind Cloudflare, Hunt used built-in analytics and found that a huge number of visitors were still trying to download JavaScript from Coinhive.
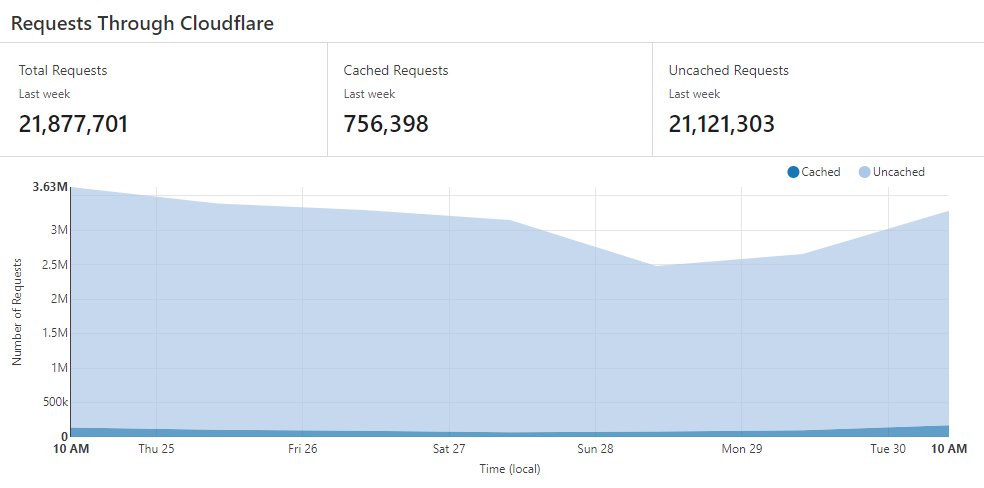
While analyzing sites that are still driving traffic to Coinhive domains, Hunt noticed that scripts are active mainly on sites in China and Russia. Most of this traffic can be attributed to hacked MikroTik routers, which continue to inject Coinhive scripts whenever users visit any site.
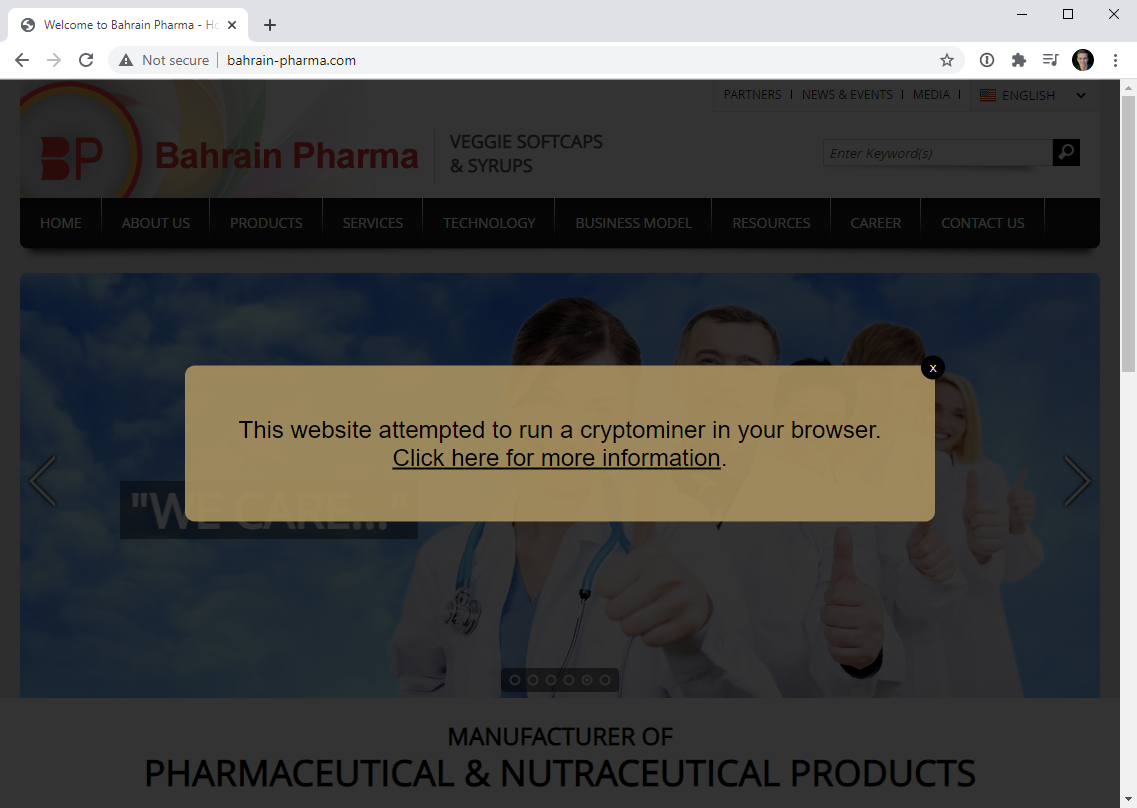
In the end, the expert decided he was using the coinhive.com domain to redirect people to his Coinhive blog post. So, if people visit sites with Coinhive scripts, they see a dialog box that will warn them: “This site tried to run a cryptominer in your browser.” Moreover, the warning is a link that users can click on and learn more about Coinhive.
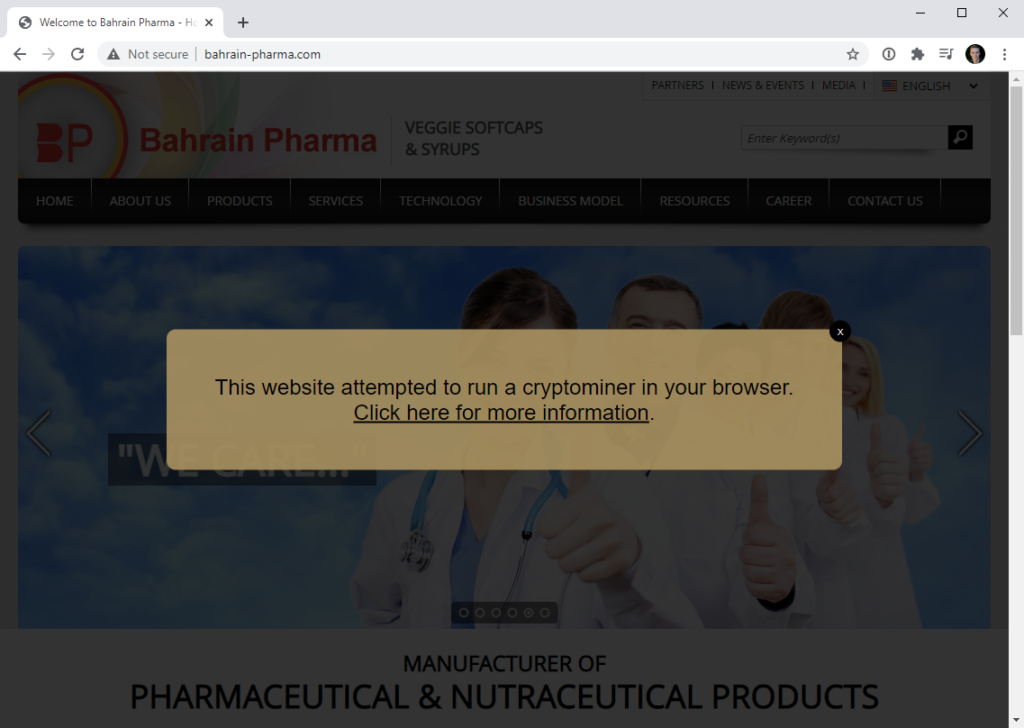
While Hunt is doing a good deed, the Coinhive example clearly shows that attackers can use abandoned domains to inject scripts into the browsers of unsuspecting visitors.