Wiz specialists discovered a problem that was given the name BingBang. They found that a misconfigured Azure Active Directory (AAD) could lead to Bing.com SERPs being compromised, XSS attacks, and Office 365 user accounts being compromised. The bug earned the researchers a $40,000 reward.
Experts have found that when building applications in Azure App Services and Azure Functions, they can be misconfigured to allow users from any Microsoft tenant, including public users, to sign in to the application.
The root of the problem lies in the Supported account types parameter, where you can specify who exactly is allowed to access the application (only personal accounts or multi-tenancy is allowed), as shown in the screenshot below.
Various configurations are provided for when developers, for example, need to make their applications available outside the organization. But if the developer loosens the restrictions by mistake, outsiders can gain access to the application and its functions. As the researchers note, “one flag is all that separates an application from multi-tenancy.”
“The architecture of shared responsibility (Shared Responsibility) is not always clear to developers, and as a result, configuration and validation errors often occur,” experts say.
Misconfigurations are so widespread that roughly 25% of all multi-tenant apps tested by Wiz are misconfigured and allow full access without proper checks.
Worse, in some cases the misconfigured applications turned out to be owned by Microsoft, which only highlights how easy it is to misconfigure Azure AD.
The key to this investigation was the discovery of a misconfigured Bing Trivia application that allowed anyone to log in and access its CMS. The fact is that this application turned out to be strained muyu is associated with Bing.com and allowed real-time replacement of the content displayed in search results.
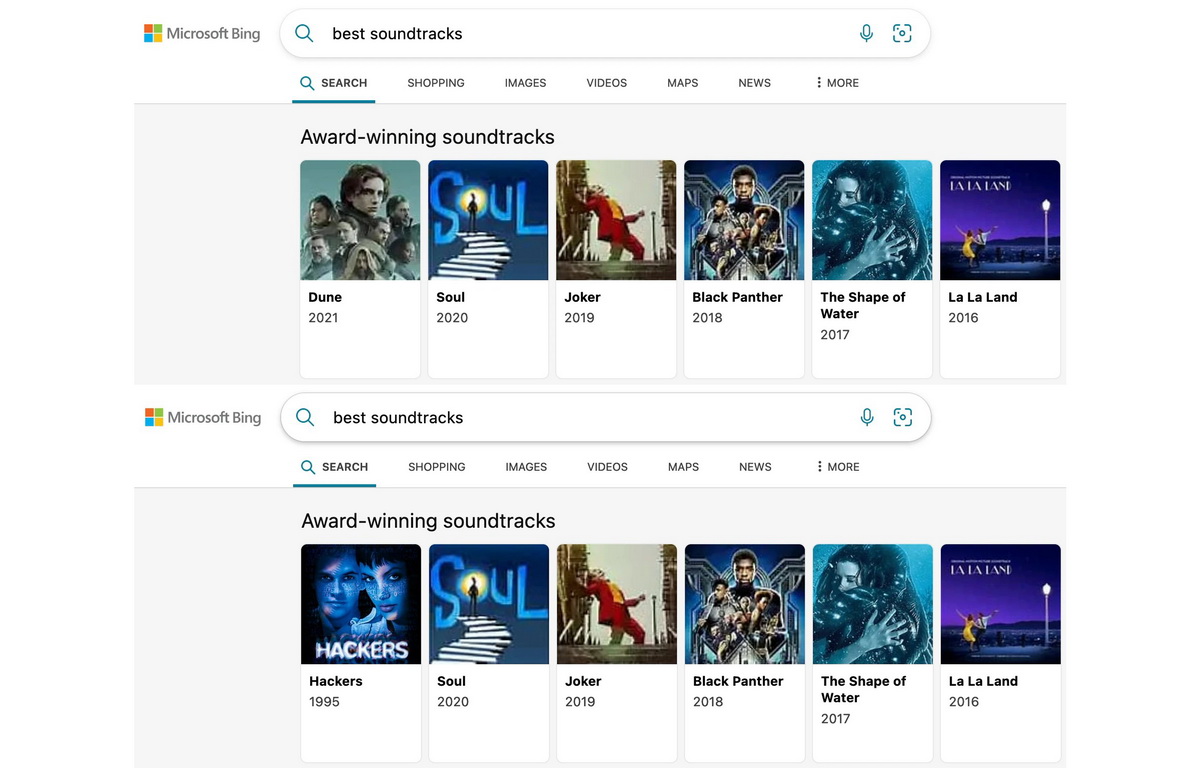
Having discovered the problem, the researchers decided to make sure that they can really influence the search results. As the video above demonstrates, they successfully changed the search results for “best soundtracks” by adding the 1995 film “Hackers” to the top carousel.
Then it turned out that the researchers could inject the payload into Bing search results using the same CMS, and they could perform an XSS attack on Bing.com. The test showed that it was possible to compromise the Office 365 token of any Bing user who saw the carousel in search results, giving a potential attacker full access to the victim’s account (including mail in Outlook, calendar, messages in Teams, SharePoint documents, and files in OneDrive).
At that time, in addition to Bing Trivia, other internal Microsoft applications were found with similar misconfigurations. These included: a control panel for an MSN newsletter called Mag News, Microsoft’s Central Notification Service API, Contact Center, an internal PoliCheck tool that looks for banned words in Microsoft code, a WordPress admin panel that allowed Wiz experts to publish fake messages on the trusted Microsoft.com domain, and finally Microsoft’s Cosmos file management system with over four exabytes of files.
Convinced that even an XSS attack is possible, the specialists rushed to report their findings to Microsoft engineers (this happened on January 31, 2023), and this week the company confirmed that the problem was finally fixed on March 28, 2023.
Microsoft now reports that a misconfiguration allowing outsiders to gain read and write access affected a small number of internal applications and was promptly fixed.
In addition, Microsoft developers claim that they have already implemented r A number of improvements that are intended to prevent the recurrence of problems with misconfigured Azure AD. Developers and administrators managing multi-tenant applications are encouraged to review the updated guidance for securing them.