A group of scientists from the Swiss Higher Technical School of Zurich has found a way to bypass PIN codes on Mastercard and Maestro contactless cards. In essence, this vulnerability allowed stolen Mastercard and Maestro cards to be used to pay for expensive products. And you don’t need a PIN.
The main idea of the attack developed by the researchers is that an attacker is introduced between a stolen card and a PoS terminal, implementing a classic MitM scenario. To do this, the offender will need:
- stolen card;
- two Android smartphones;
- a special application for Android that will help you to intervene in the fields of the transaction.
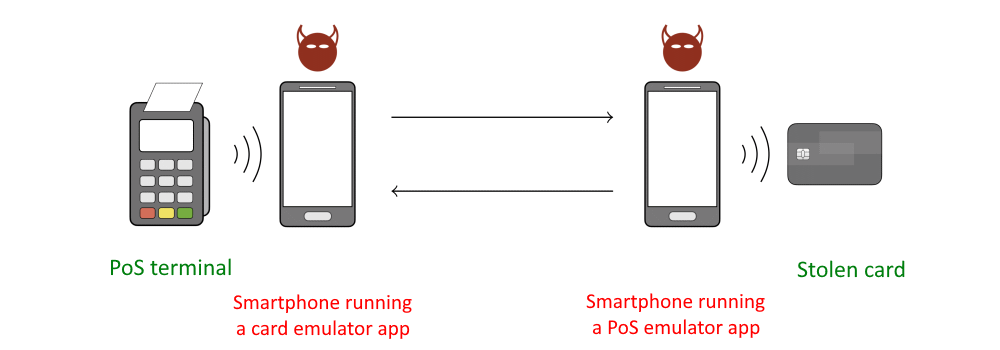
The application must be installed on both smartphones, which will act as emulators. So, one smartphone is placed next to the stolen card and will act as a PoS emulator, forcing the card to initiate a transaction and share its data, while the second smartphone will act as a card emulator and is used to transfer the “tweaked” transaction data to the store’s real PoS terminal.
As a result, from the point of view of the PoS terminal operator, such an attack is almost invisible: everything looks as if the client pays using his mobile application, while in fact the fraudster transmits modified transaction data received from the stolen card.
Experts developed this attack back in 2020 after they discovered a way to bypass PIN codes in Visa contactless payments. That attack also allowed an attacker who owns the details of a stolen contactless Visa card to use the card to pay for high-value goods, whose price far exceeds the limit of contactless transactions. And the PIN code was also not required.
Now the scientists just continued this research and focused on the issue of bypassing PIN codes on other types of cards. In a report published in early February this year and presented at this month’s USENIX conference, the research team said it had found a similar problem with contactless payments on Mastercard and Maestro cards.
The only difference is that now, instead of telling the PoS terminal that the PIN has already been verified, the researchers trick the terminal into thinking that the incoming transaction comes from a Visa card and not from Mastercard or Maestro. This is done by changing the legitimate AID of the card to AID Visa: A0000000031010.
AID spoofing activates the Visa-specific PoS terminal core, which then contacts the issuing bank to verify the card. At this point, the attacker simply carries out the old attack described last year and pays for the product without providing a PIN.
The researchers said they successfully tested such an attack with Mastercard Credit and Maestro cards, executing transactions of up to CHF 400 during the tests. A demonstration of the attack can be seen below.
The experts summarize that they have disclosed the details of the vulnerabilities to both Visa and Mastercard (which also owns the Maestro brand). And if Mastercard released fixes back in early 2021, then Visa doesn’t seem to have solved this problem yet. For this reason, the research team said it would not yet publish its Android app that facilitates such attacks. Experts fear that this could lead to massive abuse of this method of attacks and their research.





