Microsoft SharePoint servers have joined a long list of devices that ransomware uses to infiltrate corporate networks. This list also includes Citrix gateways, F5 BIG-IP balancers, Microsoft Exchange mail servers, VPN Pulse Secure, Fortinet and Palo Alto Network products.
Trend Micro experts write that the SharePoint servers are being attacked by a hack group known as Hello or WickrMe Ransomware (using Wickr accounts for messaging and negotiating ransom). These attackers were discovered by researchers at the end of 2020.
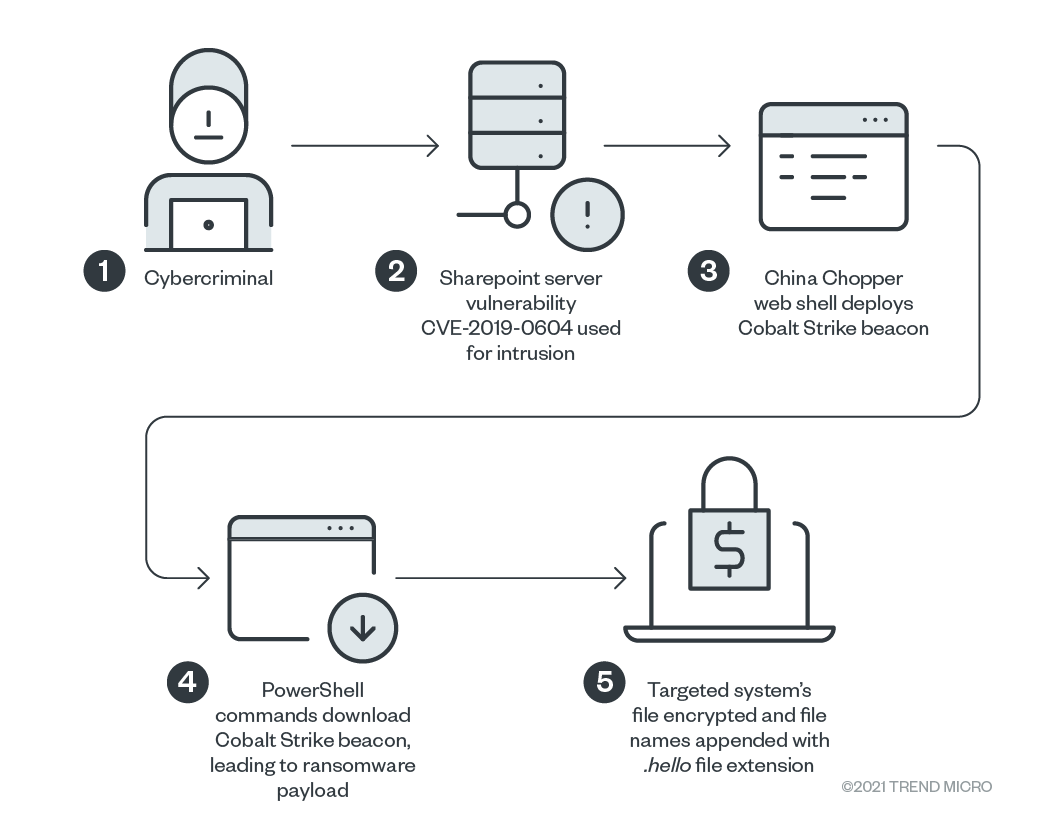
As a rule, grouping attacks are based on using an exploit for the already fixed vulnerability CVE-2019-0604 , which poses a threat to Microsoft SharePoint collaboration servers. The bug allows you to take control of the SharePoint server and install a web shell, which is then used to install the Cobalt Strike beacon (backdoor) and run automated PowerShell scripts that ultimately download and install the final payload – Hello ransomware – on the infected system.
The first attacks that attackers used SharePoint as a penetration vector were discovered in January 2021 by Pondurance , and now TrendMicro reports that these attacks continue to this day. That said, it is unclear whether hackers themselves are breaking into vulnerable SharePoint servers or simply renting access to already compromised machines from other attackers, which is a common practice for ransomware these days.