Analysts at Palo Alto Networks report that since at least October of this year, operators of the njRAT trojan have been using Pastebin as a control server to avoid the attention of cybersecurity researchers.
The company’s report states that Pastebin is being used by attackers to download and execute secondary payloads, eliminating the need for a traditional command and control server entirely.
Hacker payloads vary in form and format. So, in some cases, the dumps are base64 encoded, in other cases their true nature is hidden by hexadecimal encoding and JSON; some dumps are compressed and others are plain text containing malicious URLs.
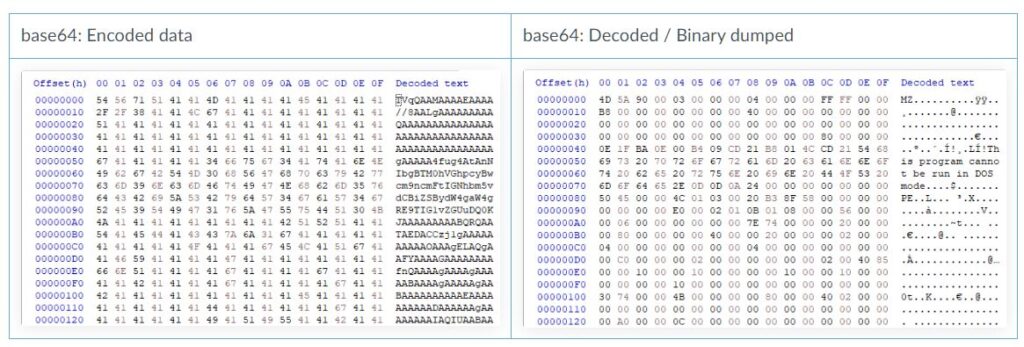
Among the samples examined by the experts, one payload turned out to be a .NET executable that abused Windows API functions for keylogging and data theft. Other samples, similar in function, required multiple levels of decoding to detect the final payload. Experts believe that JSON data can in theory be malware configuration files. Also, the content from Pastebin was used by hackers to indicate downloads of various software, including, for example, ProxyScraper.
“Based on our analysis, the malware authors are interested in hosting their second-level payloads on Pastebin, as well as encrypting or obfuscating this data to bypass security solutions.
There is a possibility that malware authors will use such Pastebin services in the long term, ”the researchers conclude.





