The researcher found a bug in the macOS Finder that allows an attacker to run commands on Mac computers with any version of macOS (up to the latest Big Sur). There is no patch for this problem yet.
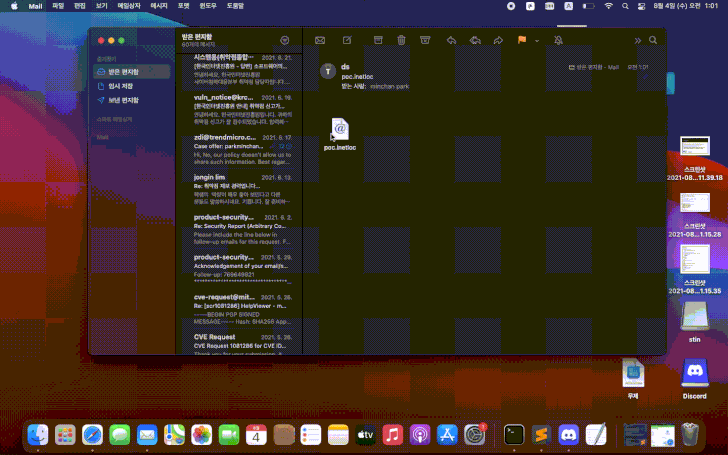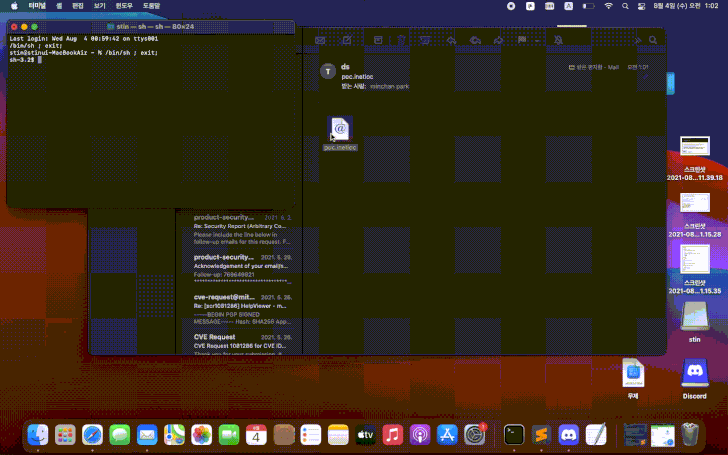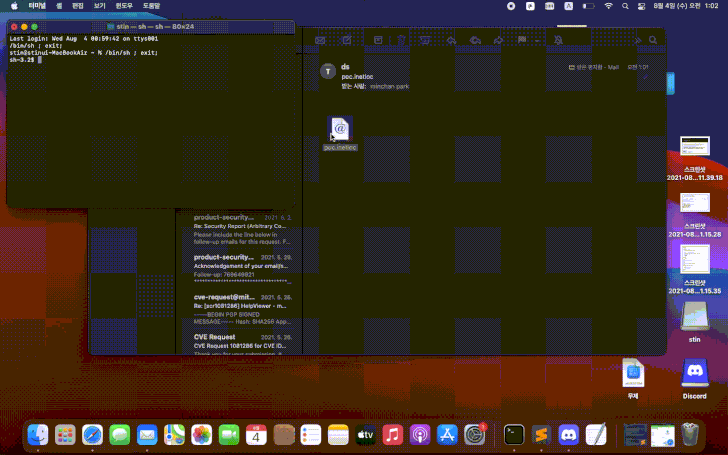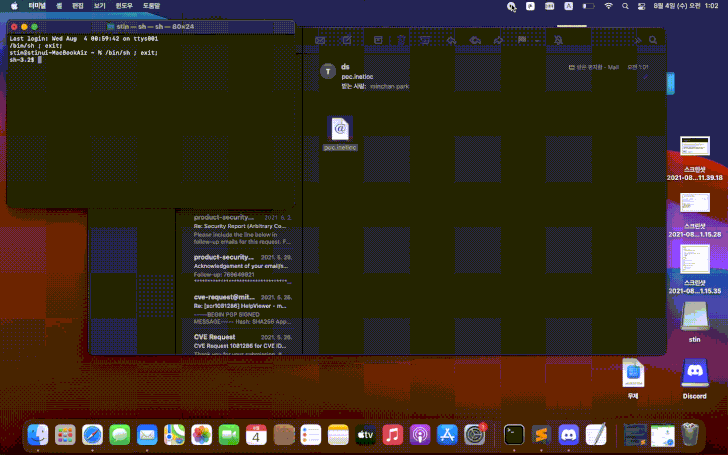
The vulnerability was discovered by independent information security expert Park Minchan, and it is related to the way macOS handles .inetloc files (Internet location files). .Inetloc files are system-wide bookmarks that can be used to open various network resources (news: //, ftp: //, afp: //) and local files (file: //). As a result, these files force the OS to run any commands embedded by the attacker without any warnings or prompts.
“Such files can be embedded in emails, which, if the user clicks on them, will execute the inline commands without displaying a prompt or warning,” warns SSD Secure Disclosure .
While Apple tried to fix the problem without assigning the CVE ID to the vulnerability, Minchan noted that the company’s patch only partially fixed the problem, and the vulnerability can still be exploited by changing the protocol used to execute inline commands from file: // to FiLe: //.
“In newer versions of macOS (Big Sur) the file: // prefix is blocked (in com.apple.generic-internet-location), but due to problems with the File: // or fIle: // case, checks are bypassed.” says the expert.
Although Minchan has already communicated his findings to Apple, he has not received a response from the company, and the vulnerability has not yet been fixed.
Edition Bleeping Computer tested the PoC-exploit provided by the researcher, and confirms that the vulnerability could be exploited to run arbitrary commands in macOS Big Sur. It is noted that attackers can abuse this bug, for example, to create malicious email attachments that will launch payloads upon opening. Even worse, so far the exploit .inetloc file is not detected by any of the solutions featured on VirusTotal.