Microsoft experts talked about a malicious campaign that has been going on for about a year. According to them, hackers change obfuscation and encryption mechanisms on average every 37 days, including using Morse code to hide their tracks and steal user credentials.
Typically, phishers’ lures are disguised as invoices related to financial business transactions, and the emails contain an HTML file (“XLS.HTML”). The ultimate goal of attackers is to collect user credentials, which are then used as a starting point for attacks.
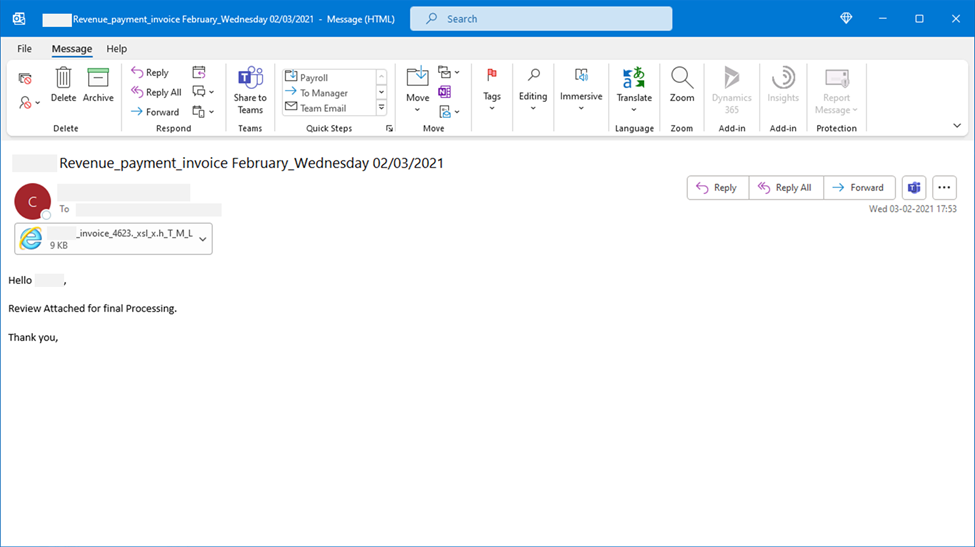
Microsoft compares the campaign to a complex jigsaw puzzle, noting that parts of HTML files look harmless and elude security products, but are then pieced together and decoded to reveal their true purpose.
“HTML attachments are divided into several segments, including JavaScript files used to steal passwords, which are then encoded using various techniques. Attackers have moved from using open HTML code to using different coding methods, including old and unusual encryption methods and Morse code, in an effort to hide fragments of attacks, “the experts write.
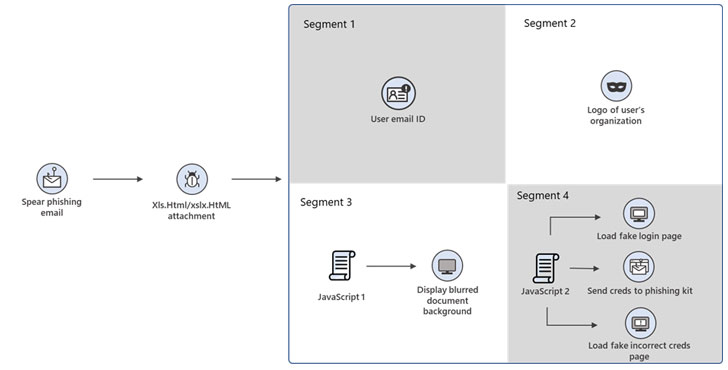
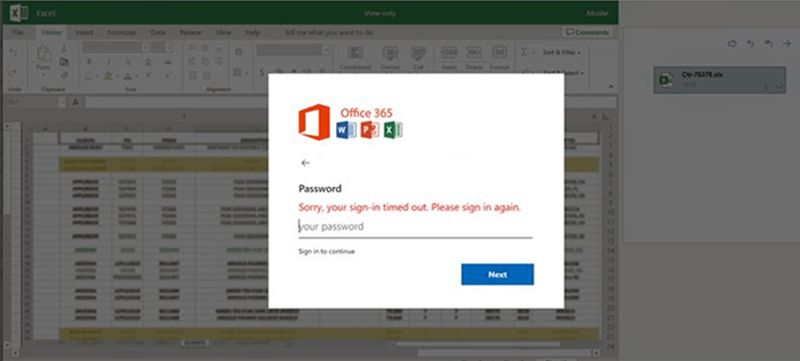
Opening a malicious attachment opens a browser window displaying a dummy window for entering Microsoft Office 365 credentials (on top of a blurry Excel document). In this window, the user is urged to sign in again because his access to the Excel document has supposedly expired. If a person falls for the bait of scammers and enters a password, he receives a message that the entered password is incorrect, while in fact the malware steals data unnoticed.
The researchers report that these attacks began in July 2020, and since then, the campaign has undergone about ten iterations, during which the attackers changed their encoding methods to disguise malicious HTML attachments.
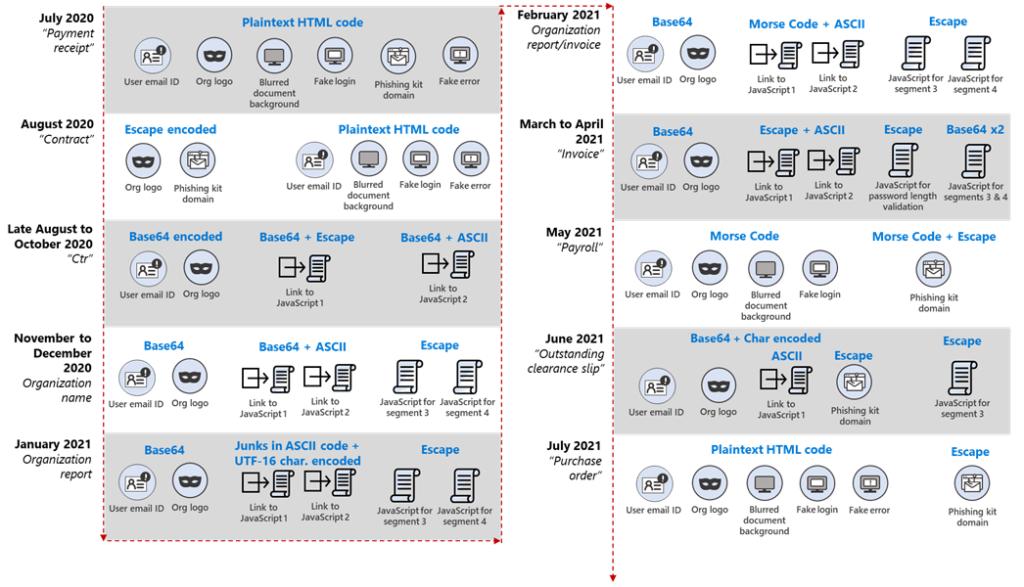
“Morse code is an old and unusual encoding method that uses dashes and dots to represent characters. This mechanism was used in the February and May attacks, writes Microsoft. – In the February iteration, JavaScript file references were encoded using ASCII and then Morse code was used. Whereas in May the domain name in the phishing kit URL was Escape-encoded before all HTML was encoded using Morse code. “
Let me remind you that in February of this year, Bleeping Computer warned about the use of Morse code by phishers.




