Researchers at Secureworks have discovered a strange precedent: the developers of the LV ransomware seem to have coiled and modified the binaries of the more famous hack group REvil.
According to experts, LV operators somehow managed to get their hands on the binary that is responsible for the actual encryption during the REvil attacks. The hackers then used a hex editor to modify this binary and its configuration file. The result of these modifications, in fact, has become a new version of the REvil ransomware, which security experts have been discovering since the beginning of 2021 and are tracking under the name LV.
Analysts write that the similarities between the LV and REvil sources were immediately obvious, but now they have examined the LV code in more detail. So, it turned out that even the remnants of a code block in which REvil insults two well-known malware analysts have been preserved in LV.
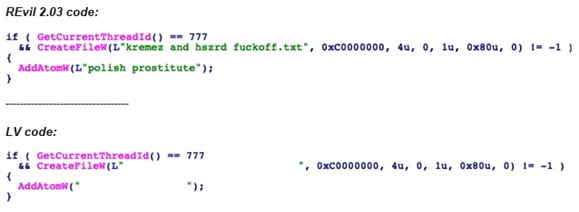
Secureworks concludes that LV operators appear to have modified the beta version of REvil 2.03, which eventually became the LV ransomware. At the same time, it is noted that, despite the theft of the malware code, the LV hack group is still not like REvil in terms of internal infrastructure. For example, LV removed from the code the C&C servers that REvil used to track infections, but did not replace them with its own, leaving this section blank.
“LV may not be able to maintain the management infrastructure and develop the internal automation needed to process and track victim data,” experts say.
It has also been observed that the group’s darknet sites, where LV victims are asked to pay a ransom, often fail and return errors when victims or analysts try to access them. Secureworks believes this may indicate that LV is “struggling to maintain a resilient infrastructure, but suffers from a lack of skills or resources.”
In addition, LV has tried to mimic REvil by creating its own “leak sites” where hackers threaten to publish victims’ data if they do not pay the ransom. Many cybercriminals do this, but Secureworks notes that the group never shared information about its victims, listed on the “leak sites”, to anyone. That is, in fact, the group may not have the ability to store the stolen data at all.
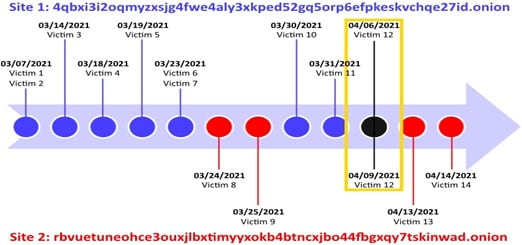
At the same time, LV had two such sites for leaking information, and each of them listed different victims, with the exception of one entry. Why this was done is still unclear.
As for the REvil gang, Secureworks believes that the binary piracy incident could push the group to make the code more complex and increase security (in order to prevent possible modifications to the configuration files in the future), which could significantly complicate the work of information security experts.




