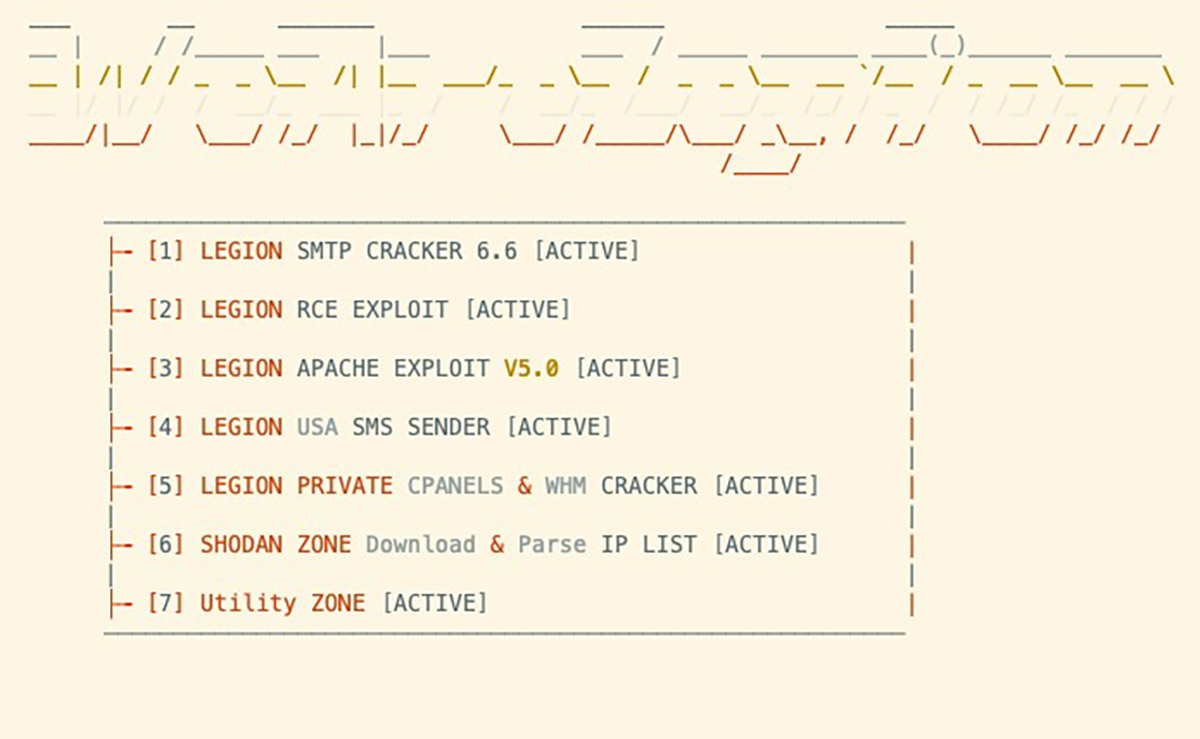
Experts have discovered a Legion hacking tool based on Python. The malware is sold via Telegram and is used to hack various online services for further exploitation. According to Cado Labs researchers, the malware has modules for listing vulnerable SMTP servers, conducting remote code execution (RCE) attacks, exploiting unpatched versions of Apache, brute-forcing cPanel and WebHost Manager (WHM) accounts, as well as interacting with the Shodan API and abusing AWS services.
The researchers say the malware shares similarities with another malware family, AndroxGh0st, which was first discovered by cloud security provider Lacework in December 2020. Last month, SentinelOne published an analysis of AndroxGh0st, which showed that the malware is part of the AlienFox toolkit, which is offered to criminals to steal API keys and secrets from cloud services.
Legion is part of a new generation of cloud credential harvesting and spam utilities. The developers of these tools often steal code from each other, making attribution difficult. In addition to using Telegram to extract data, Legion is designed to hack web servers with CMS, PHP, or PHP-based frameworks such as Laravel. It is capable of obtaining credentials for a wide range of web services such as email providers, cloud providers, server management systems, databases, and payment platforms, including Stripe and PayPal. Other targeted services include SendGrid, Twilio, Nexmo, AWS, Mailgun, Plivo, ClickSend, Mandrill, Mailjet, MessageBird, Vonage, Exotel, OneSignal, Clickatell, and TokBox.
Legion also extracts AWS credentials from insecure or misconfigured web servers and sends spam SMS to users of US carriers, including AT&T, Sprint, T-Mobile, Verizon, and Virgin. The main purpose of the malware is to use the infrastructure of hijacked services for subsequent attacks, including bulk spam and opportunistic phishing campaigns.
The researchers also discovered a YouTube channel (created June 15, 2021) containing tutorial videos on Legion. This indicates that the tool is widespread and most likely is paid malware. The location of the creator of this tool, who uses the Telegram nickname forzatools, remains unknown, although the presence of comments in Indonesian in the code suggests that the developer may be Indonesian or located in that country.