German law enforcement officers confiscated the servers of FlyHosting, a darknet resource intended for criminals involved in organizing DDoS attacks for hire. FlyHosting had been advertised on hack forums, claiming to be open to anyone looking for a secure place to host malware, manage botnets, or DDoS infrastructure.
On March 30, 2023, the German Federal Criminal Police Office (Bundeskriminalamt, BKA) issued eight search warrants and identified five people aged between 16 and 24 who were suspected of using the “Internet service” since mid-2021. The authorities have not yet disclosed the names of the suspects or the name of the Internet service in question.
According to the BKA, “previously unknown criminals” had used the Internet service provided by the suspects to organize DDoS attacks. As a result, the websites of various companies, as well as the websites of the Hesse police, had been overloaded in several cases, making them “only be used to a limited extent or not at all.”
Last week, information security journalist Brian Krebs reported that the first news about the raid on FlyHosting had appeared in a Telegram channel frequented by people involved in the DDoS-for-hire industry.
“Flyhosting has migrated its systems to the new police premises ;),” wrote a user with the nickname Dstatcc. “We expect the police to scrutinize files, payment logs, and IP addresses. If you’ve used their server and [the police] can find ‘bad things’ related to you (paid for through your personal PayPal), you should contact a lawyer.”
The authorities said in a statement that during the searches, police confiscated mobile phones, laptops, tablets, various storage media, and handwritten notes from the defendants, as well as servers they operated in Germany, Finland, and the Netherlands. Law enforcers confirmed to Brian Krebs that the confiscations and raids were related to FlyHosting.
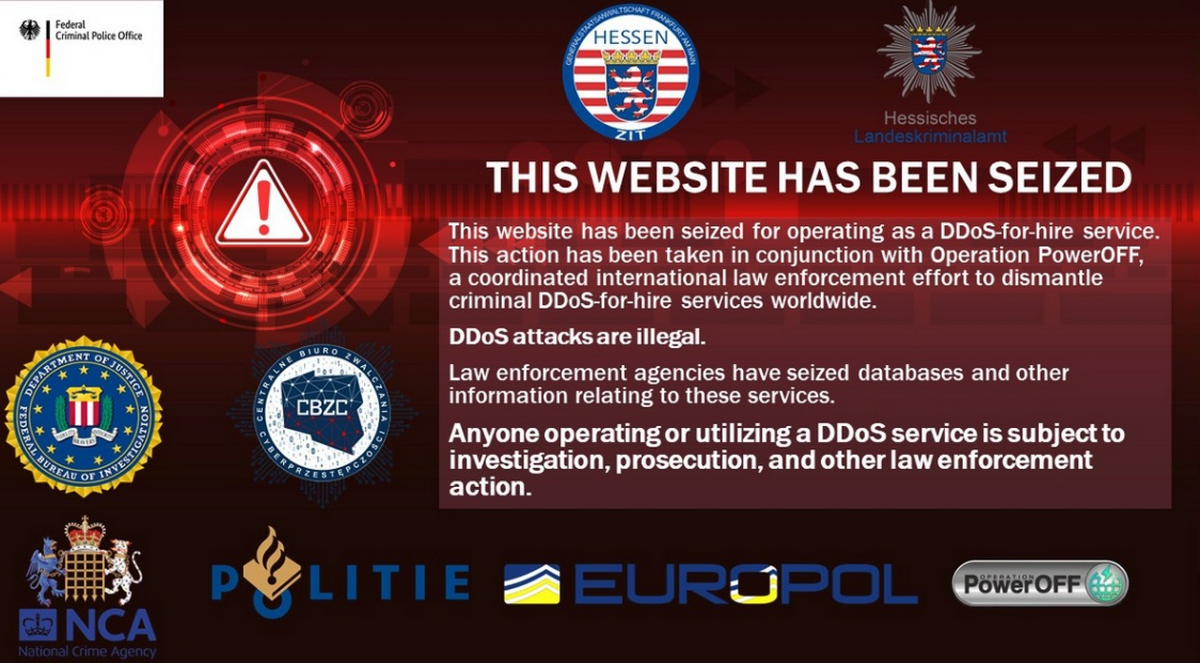
The actions against FlyHosting are likely connected to a large-scale international law enforcement operation called PowerOff, which aims to eliminate criminal DDoS infrastructures for hire around the world. For example, at the end of 2022, as part of this operation, 48 domains were confiscated and closed, and charges were brought against six suspects who were involved in operating platforms for DDoS attacks for hire.
The British National Crime Agency (NCA) also reported that, as part of the PowerOff operation, they had created a network of fake sites where people could allegedly order a DDoS attack. This allowed the NCA to identify people who wanted to use DDoS services and use these platforms for attacks.