ThreatIT Reports for the second time after ThreatIT first article about CyberPunk2077 and after Kaspersky Lab specialists discovered malware that was disguised as a beta version of Cyberpunk 2077 for Android and was distributed via cyberpunk2077mobile [.] Com.
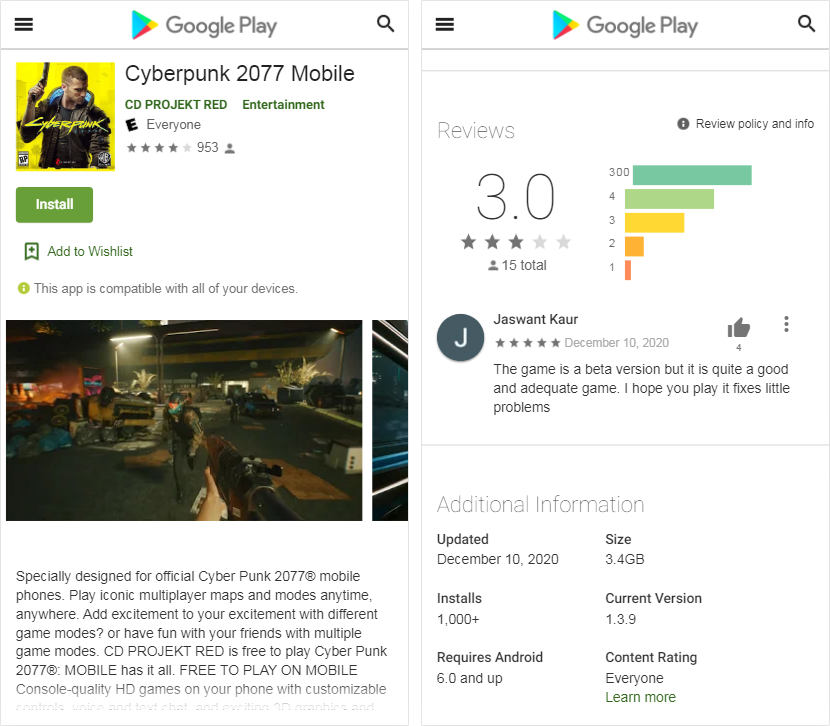
The site of the “mobile version” looked suspiciously like Google Play, and its creators claimed that the beta was released on the day the game was officially released. Allegedly, the “beta” has already been downloaded by about a thousand people, and some of them even left feedback, noting that the game is not bad for the beta version.
CYBER PUNK IS A MALWARE !
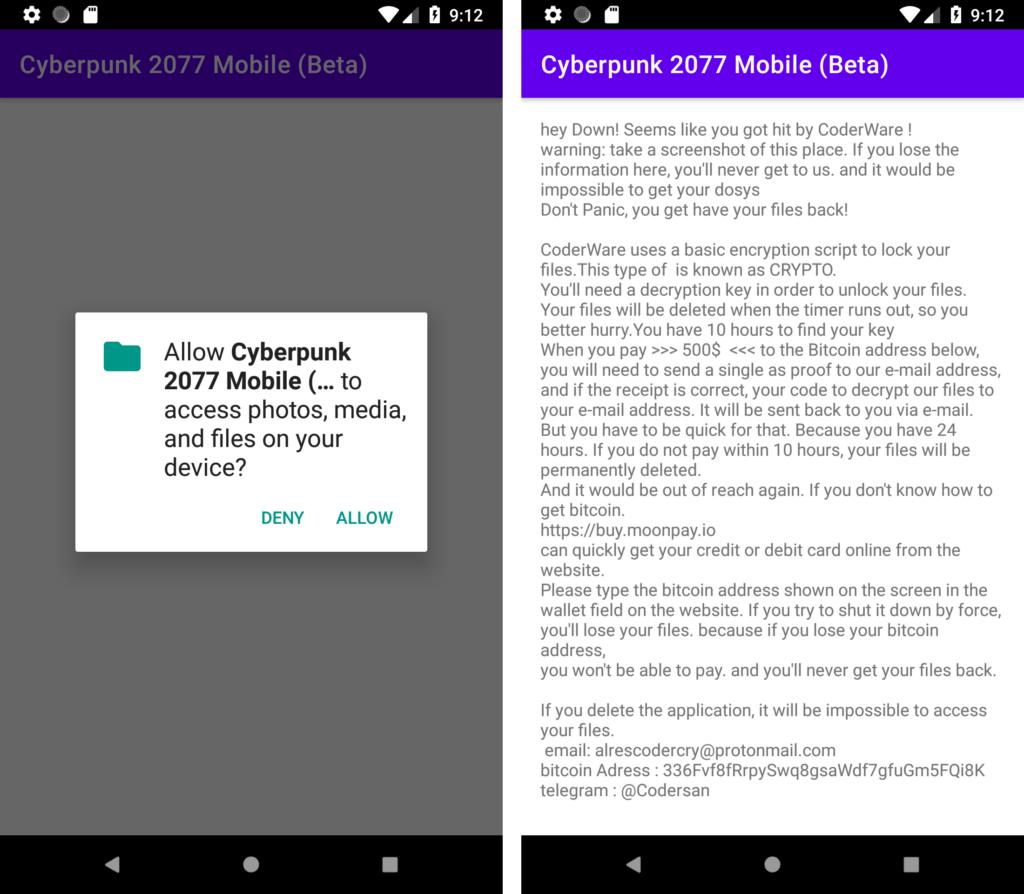
Although the website states that the application weighs 3.4 GB, when downloading the file, the file does not even reach 3 MB. When starting the application, first of all, it requires access to files on the device. In theory, the application may need these rights if the user wants to save or open something through it, but the game hardly needs photos and videos to start. However, the application cannot run without this permission. However, even if you give out all the rights to the fake, you won’t be able to play either: instead of Cyberpunk 2077, the victim will only see a message demanding a ransom.
CYBER PUNK LINKED WITH CRIMINALS AND CRYPTO CURRANCY
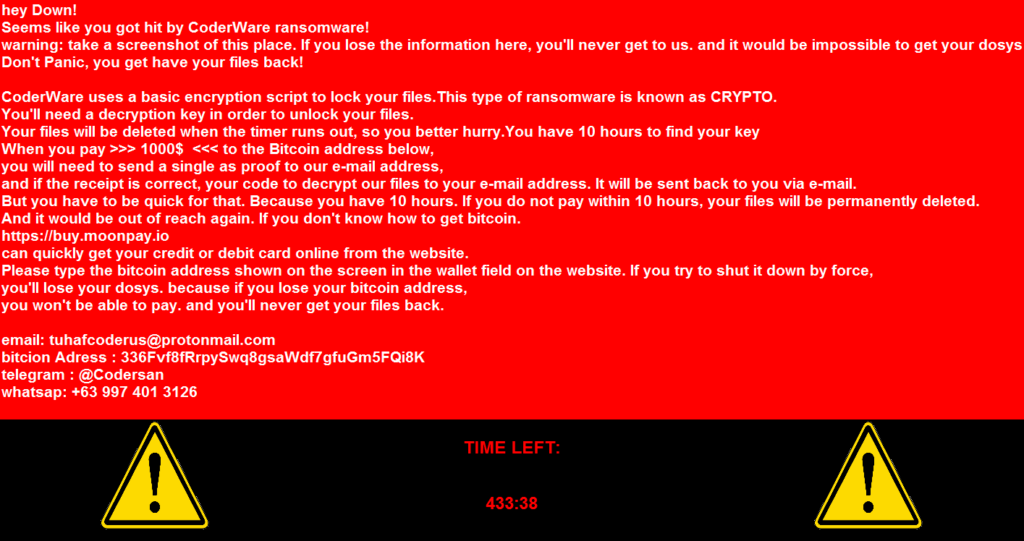
In a note in broken English, the user is explained that now all his photos and other important files are encrypted. To restore them, you need to transfer $ 500 in bitcoins to the cybercriminals’ wallet. Otherwise, the malware will permanently delete the data and it will be impossible to recover it. It is also impossible to get rid of the ransomware, according to the ransomware: the files allegedly cannot be returned.
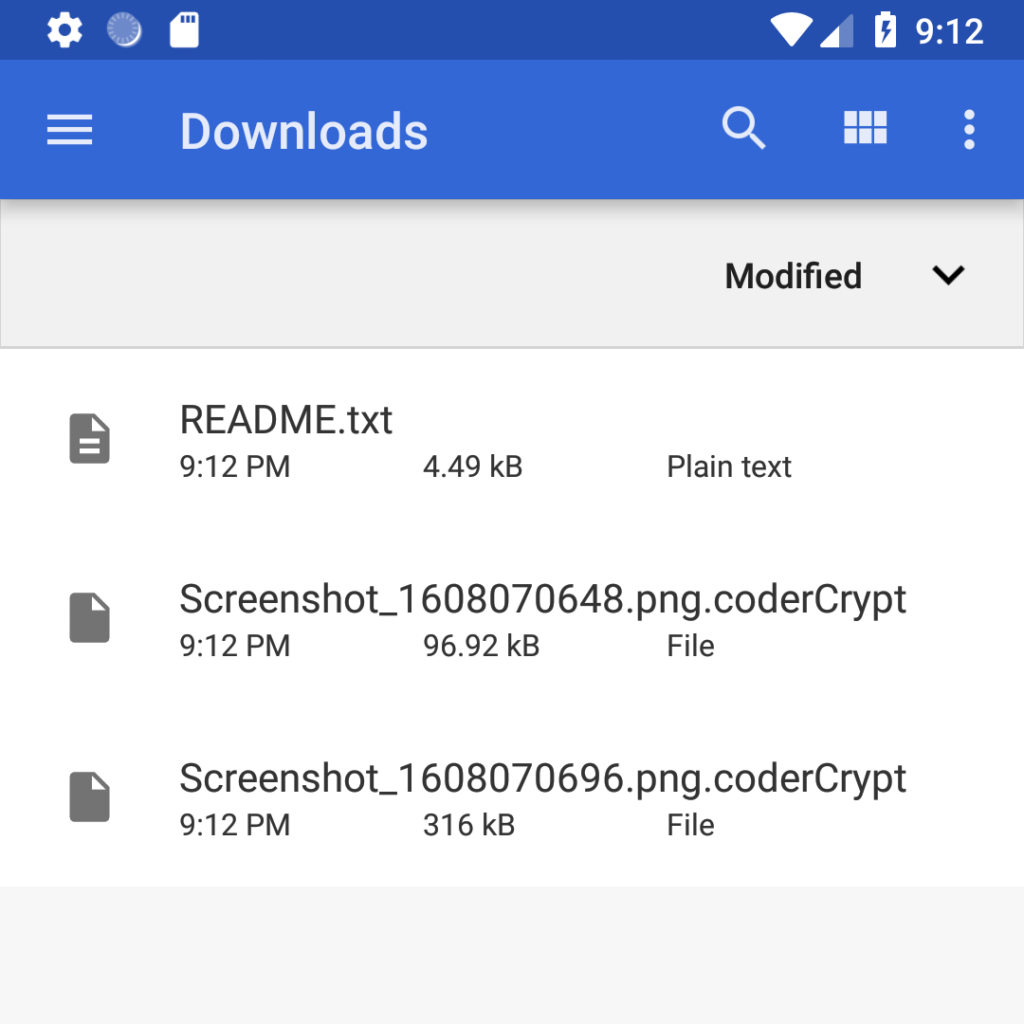
The researchers checked what actually happens to the files on the infected device. The threats were not empty: the files were indeed encrypted and assigned the .coderCrypt extension. In addition, the malware placed a README.txt file in each folder with the same note as in the application window.
However, it turned out to be possible to recover the files without the help of malefactors. The fact is that the malware uses the RC4 symmetric encryption algorithm. That is, to decrypt the data, you need the same key with which they were encrypted. In this case, the key was hardcoded into the application code. In all the samples that the experts came across, the key was: “21983453453435435738912738921”.
ANDOIRD RANSOMWARE
Experts also write that the authors of the fake beta Cyberpunk 2077 for Android are also distributing an encryptor for Windows disguised as the same game. The files encrypted by it can no longer be restored on their own, because the key is not hard-coded into the application code, but is randomly generated for each individual infection case. Perhaps this is precisely why they demand twice as much money from PC users as from victims of mobile malware.