An open repository was found on GitHub, the contents of which are very similar to the Cobalt Strike source code crack.
In less than two weeks of existence, the repository has created 172 forks. Stopping the further spread of the toolkit popular with cybercriminals will likely be difficult. The Cobalt Strike framework is quite legitimate; it is a set of post-exploitation tools that allow you to create shells, remotely execute PowerShell scripts, escalate privileges, and more. Information security professionals typically use Cobalt Strike for penetration testing.
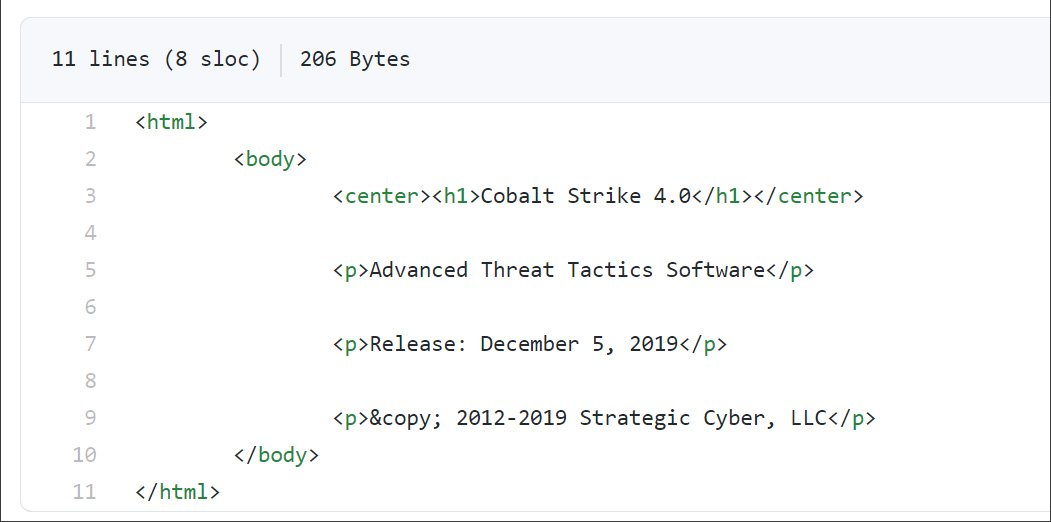
The toolkit’s capabilities were also appreciated in criminal circles: the authors of targeted attacks often use it to secure remote access to a compromised network. An analysis of the code posted in the Git repository revealed a great similarity to the Cobalt Strike source. Based on the content of the about.html file, this is version 4.0 of the toolkit.
The author of the find believes that this Java code was decompiled by hand. Some dependencies have been tweaked and license checking has been removed.
While not the original Cobalt Strike, publishing the source can have very serious consequences: it lowers the bar for inexperienced hackers. Moreover, having access to the code, attackers will begin to improve it at their own discretion, and the number of sophisticated targeted attacks will increase significantly.
In September, the source code of the Android Trojan Cerberus was leaked online . Then unknown people posted it on the darkweb sites. And at the beginning of October, the code of the operating systems Windows XP and Windows Server 2003 surfaced on 4chan, the authenticity of which was confirmed almost immediately.