At the SAS 2021 conference, Kaspersky Lab analysts spoke about the tools of the new Chinese cyber-espionage group GhostEmperor, which has been attacking large organizations in Southeast Asia since at least July 2020.
The names of the affected companies were not disclosed, but researchers report that GhostEmperor attacked government agencies and telecommunications companies in Southeast Asia (Malaysia, Thailand, Vietnam and Indonesia), as well as in Egypt, Afghanistan and Ethiopia.
The experts reported that GhostEmperor uses very sophisticated tools and mainly focuses on gaining and maintaining long-term network access to its goals. For this, in particular, a special rootkit is used that works even with the latest versions of Windows 10.
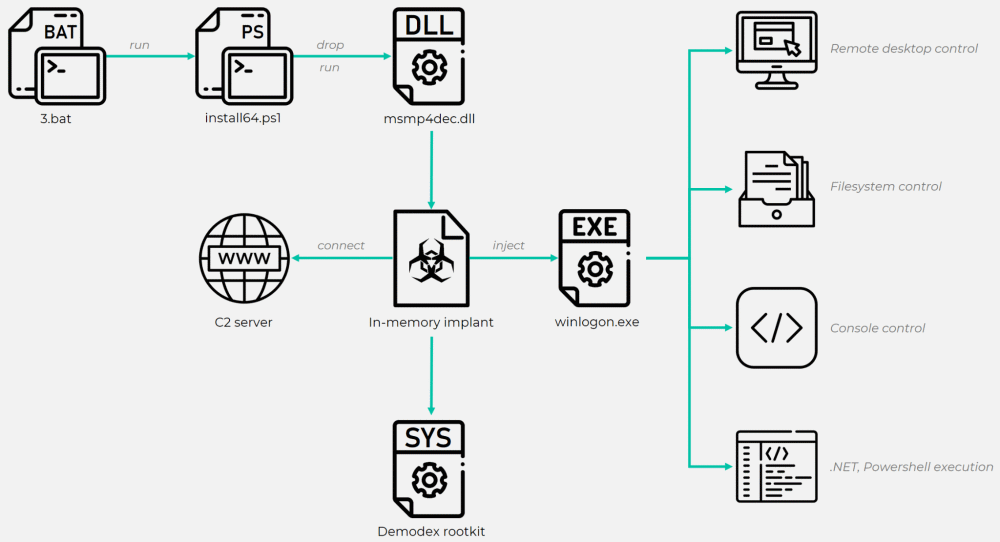
As a rule, the public servers become the point of initial penetration into the victim’s network for the GhostEmperor. Analysts observed that in order to compromise them, the group used exploits for vulnerabilities in Apache, Oracle and Microsoft Exchange, and then came to hack other systems on the victim’s network.
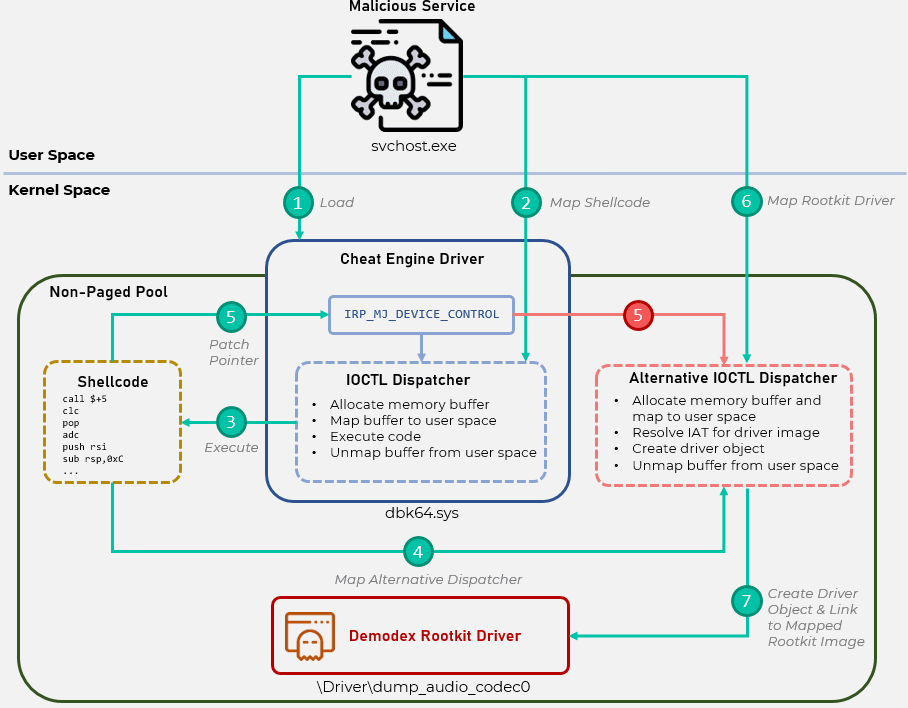
Hackers are also known to use a set of different scripts and tools to deploy backdoors to victims’ networks. This backdoor is then used to download and run the Cheat Engine tool, often used by gamers to inject cheats. However, the hackers used powerful Cheat Engine drivers to bypass the Windows PatchGuard security features and install the Demodex rootkit on the victim’s OS. Experts call this rootkit very advanced, as it allows hackers to retain access to the victim’s device even after reinstalling the OS and even on systems with the latest versions of Windows 10.
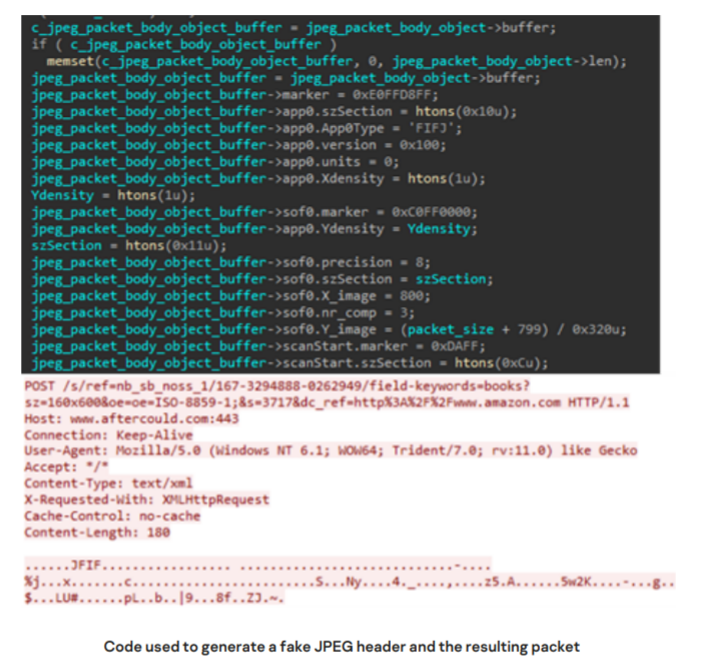
In addition, it is noted that the group’s malware is replete with sophisticated methods of protection against forensics and analysis, which should interfere with information security specialists trying to analyze the GhostEmperor toolkit. Another clever hacker trick: repackaging data into fake multimedia formats. As a result, the traffic of the GhostEmperor malware is usually disguised as RIFF, JPEG or PNG files.