Sentinel Labs has discovered the Aoqin Dragon hacker group, which is engaged in cyber espionage, attacking government, educational and telecommunications organizations in Singapore, Hong Kong, Vietnam, Cambodia and Australia. Analysts have been lucky to link the hackers to malicious activity dating as far back as 2013.
Aoqin Dragon managed to remain virtually unnoticed for ten years, with only a fraction of the hackers’ activity falling into the old reports of information security companies. Experts write that the group has achieved such secrecy by constantly improving their methods and changing tactics. And now, with the release of the Sentinel Labs report, it’s likely to happen again.
During this time, Aoqin Dragon used three different tactics to infect the systems of its targets, according to the researchers. The oldest tactic, used between 2012 and 2015, exploited Microsoft Office documents and known vulnerabilities, including CVE-2012-0158 and CVE-2010-3333.
Such attacks were spotted by FireEye in 2014 while studying a spear phishing campaign by the Chinese hack group Naikon APT targeting government agencies in the Asia-Pacific region and a think tank in the United States.
The second tactic is disguising malicious executables with fake antivirus icons to trick the user into launching and activating the malware dropper.
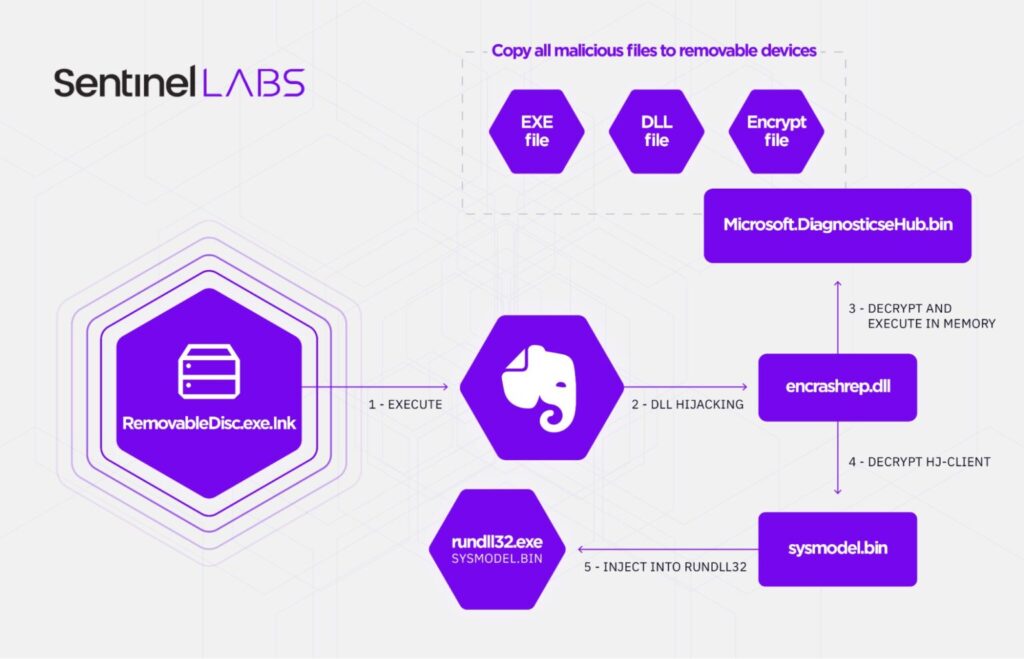
A third tactic that Aoqin Dragon has been using from 2018 to the present is exploiting removable drive shortcuts that, when clicked, cause DLL hijacking and download an encrypted backdoor payload. This malware is called Evernote Tray Application and runs at system startup. If the bootloader detects available removable devices, it copies the payload to them as well in order to infect other devices on the target network.
Sentinel Labs has identified two different backdoors used by this hack group: Mongall and a modified version of Heyoka. Both are DLLs that are injected into memory, decrypted, and then executed.
Mongall has been in development since at least 2013, and the latest versions feature an updated encryption protocol and Themida wrapper designed to protect against reverse engineering. The main purpose of this malware is to profile the infected host and send the collected data to the command and control server via an encrypted channel. Although Mongall can also perform actions on files and run shells.
The second backdoor, Heyoka , is an open source data mining tool that uses fake DNS queries to create a bi-directional communication tunnel. This tool is used by hackers to copy files from compromised devices to make it harder for defenders to detect data theft.
At the same time, the developers of Aoqin Dragon modified Heyoka, turning it into a backdoor with support for the following commands:
- open shell;
- get information about the host disk;
- file search;
- create a file;
- create a process;
- get all information about the processes on the host;
- terminate the process
- create a folder;
- delete file or folder.
“Based on our analysis, victims, infrastructure, and design of the Aoqin Dragon malware, we are quite confident in assessing this threat as a small Chinese-speaking hack group that may be related to APT Naikon and UNC94,” Sentinel Labs researchers conclude.





