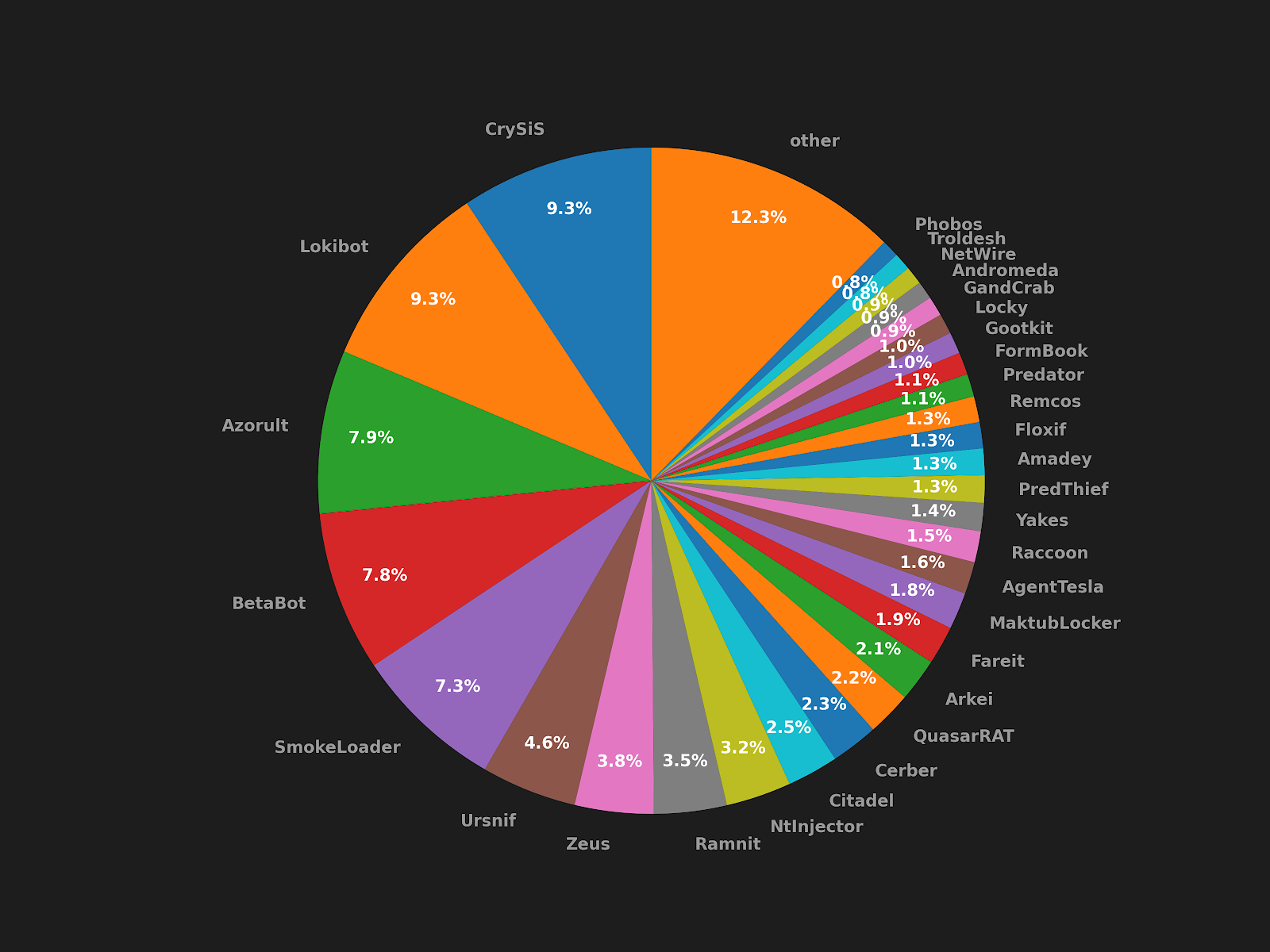
Avast Threat Labs researchers report on the OnionCrypter cryptor, which has been widely used by many malware families since 2016, including Ursnif, Lokibot, Zeus, AgentTesla, and Smokeloader. It helps hide malicious pieces of code using encryption to make it harder to detect and analyze.
According to the company, over the past three years, Avast has protected nearly 400,000 users worldwide from malware that used this cryptor. The diagram below shows which malware families using OnionCrypter have already been detected by Avast.
Experts write that the structure of modern malware is very similar to the structure of a car: it also consists of many parts. Only instead of the engine, wheels and steering wheel, such programs have a bootloader, payload and command module.
One of these “details” is often the cryptor, which helps to hide the malicious parts of the code using encryption, and as a result, the code may seem harmless at first glance, and it will be more difficult to read. For malware developers, cryptor is an important tool for countering protection. At the same time, for researchers, the detection of the cryptor makes it faster to find and identify new malware that contains it.
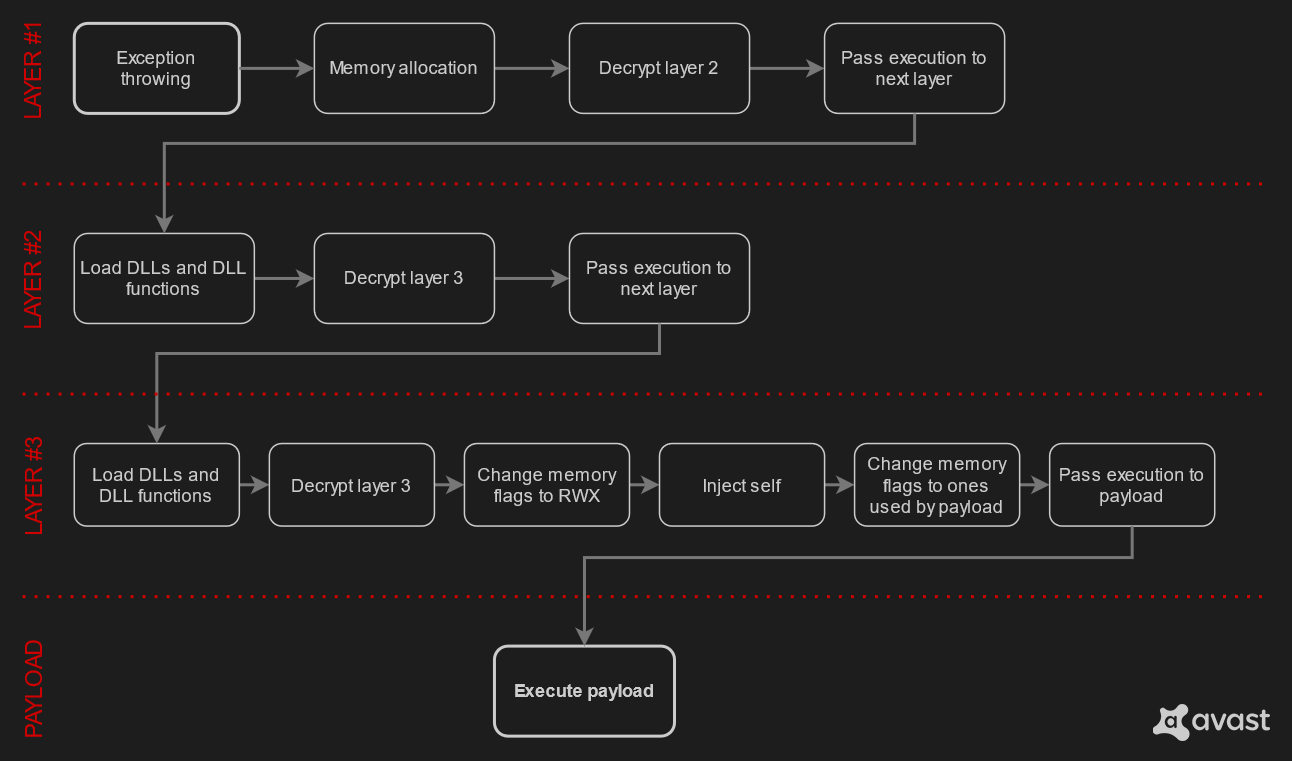
The name OnionCrypter has nothing to do with Tor (network or browser) and is a reference to an ordinary onion: a cryptor, like an onion, consists of many layers of encryption that protect information from researchers, antiviruses and security solutions. It is this layering that makes OnionCrypter so unusual.
As you can see in the illustration below, the OnionCrypter architecture is complex and consists of three layers. In the company’s report, a separate and detailed section is devoted to each of them.
Considering the rather long time of use and the prevalence of OnionCrypter, experts have come to the conclusion that the developers are selling it as a service. In addition, OnionCrypter’s makers seem to be offering buyers a custom tweak to make it even less noticeable. In advertisements on hacker forums, OnionCrypter is often referred to as “completely invisible.”
Now, the information obtained by Avast researchers will greatly simplify the task of detecting OnionCrypter and any malware that uses it.