Recently at the Black Hat conference, they talked about the remote code execution vulnerabilities in Microsoft Exchange, collectively known as ProxyShell. Now experts are warning that hackers are already scanning the Internet for vulnerable devices.
The name ProxyShell combines three vulnerabilities that allow unauthenticated remote code execution on Microsoft Exchange servers. These vulnerabilities are exploited by Microsoft Exchange Client Access Service (CAS) running on port 443.
- CVE-2021-34473 : Unauthenticated Path Confusion leading to ACL bypass (fixed in April in KB5001779 );
- CVE-2021-34523 : Exchange PowerShell Backend privilege escalation (fixed in April in KB5001779 );
- CVE-2021-31207 : Writing arbitrary files after authentication, leading to remote code execution (fixed in May in KB5003435 ).
Although CVE-2021-34473 and CVE-2021-34523 were first disclosed in July, in fact, they were quietly fixed back in the April Microsoft Exchange cumulative update KB5001779. The fact is that these problems were discovered by researchers at Devcore, whose team received a prize of $ 200,000 for their use in the April 2021 Pwn2Own hacking competition . Now Devcore specialists made a presentation at Black Hat and talked about the vulnerabilities of Microsoft Exchange in more detail, and after the speech they even published a detailed article about ProxyShell.
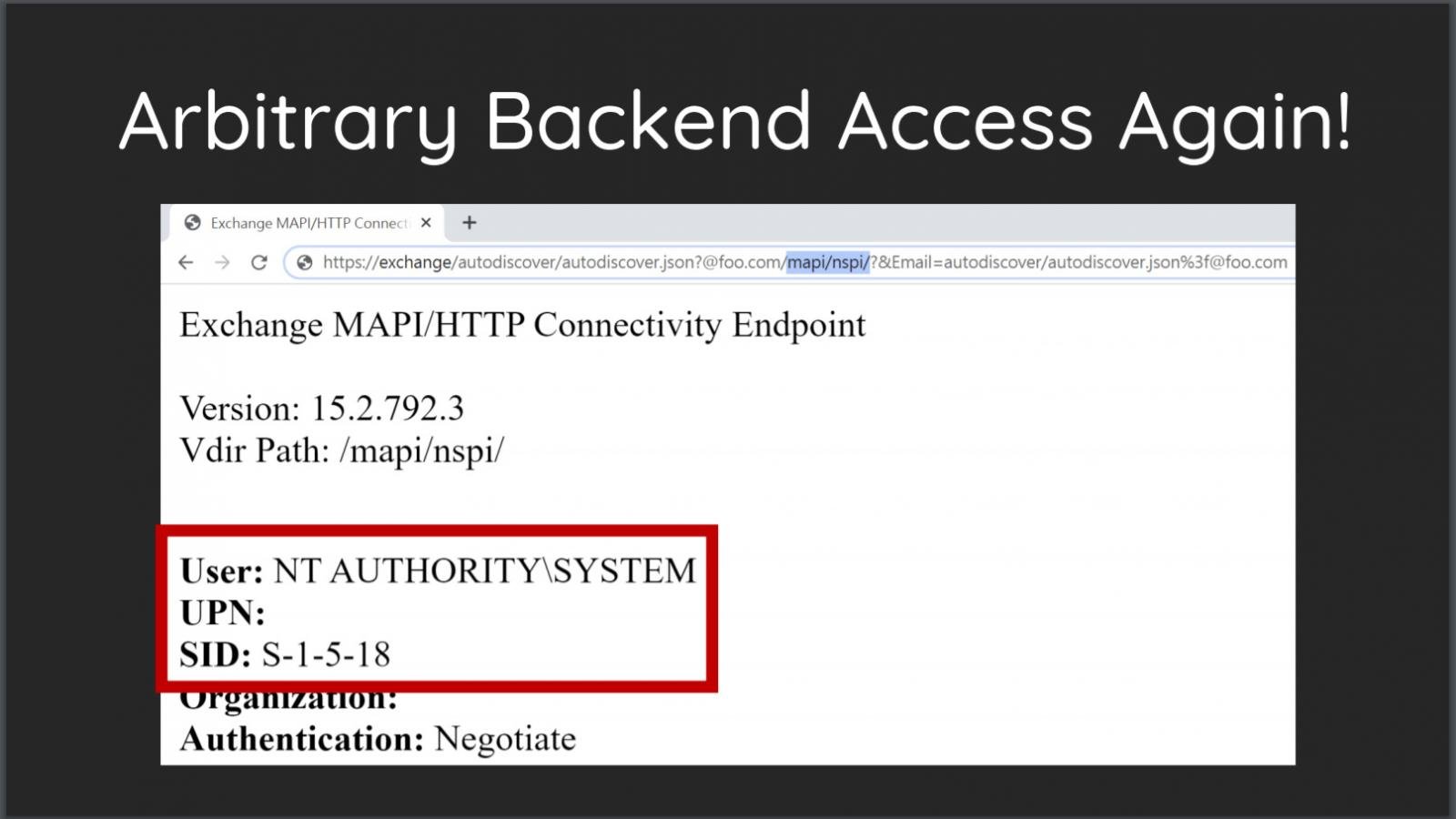
The researchers said that one component of ProxyShell targets the Microsoft Exchange Autodiscover service, which is used by an email client as an easy, automatic configuration method with minimal user intervention.
After the publication of the experts’ article, the hackers began scanning the network in search of devices vulnerable to ProxyShell. Well-known information security researcher Kevin Beaumont writes on Twitter that administrators should use Azure Sentinel to check the IIS logs for the lines “/autodiscover/autodiscover.json” or “/ mapi / nspi /”, as this means that attackers scanned the server for subject of vulnerability. Beaumont also reminds that the patches are already available and recommends installing them as soon as possible.