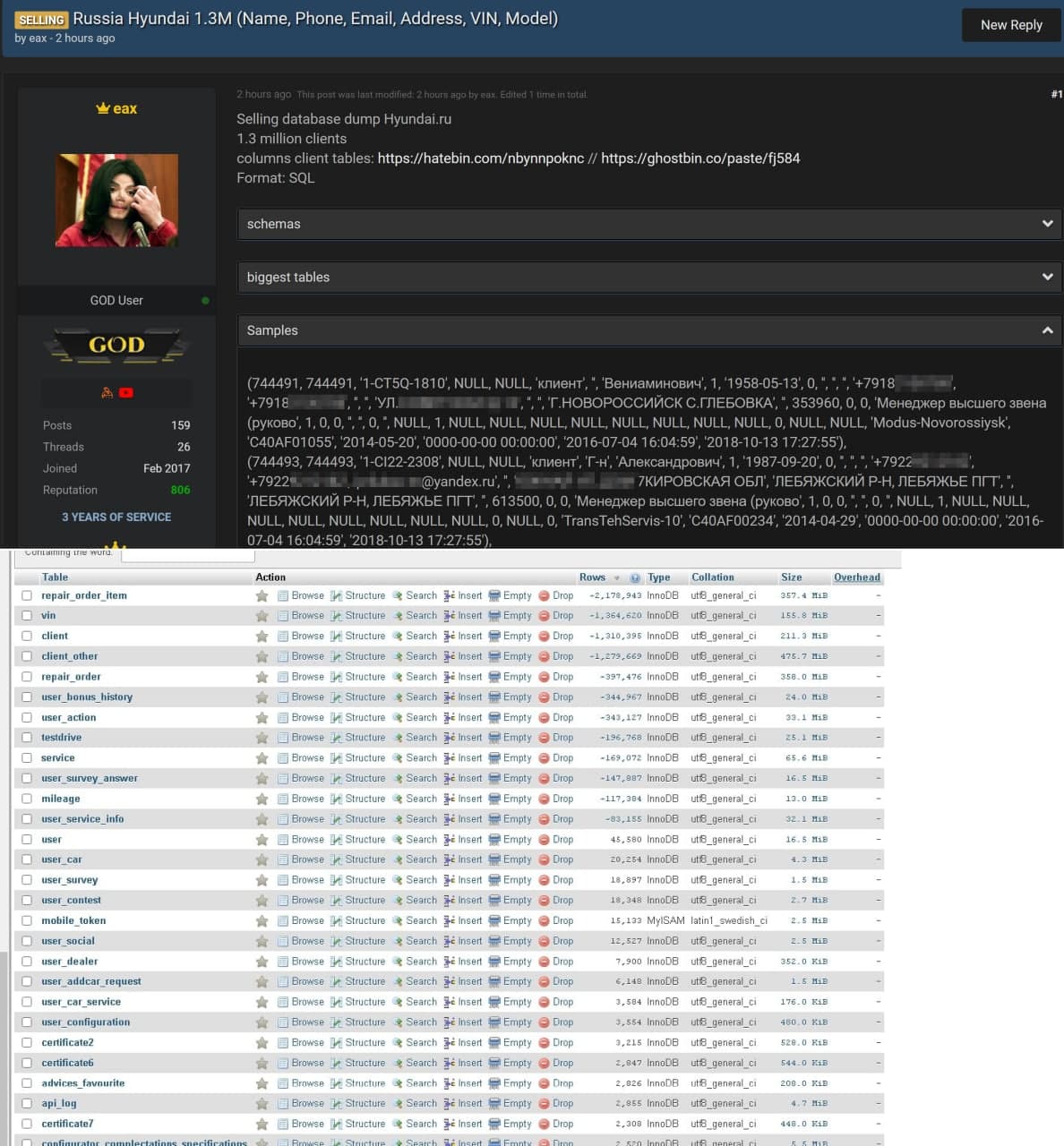
The hyundai.ru user database is up for sale on the shadow forum
According to the telegram channel of information leakage , an announcement on the sale…
Attackers start using Zyxel backdoor account in attacks
Cyber criminals scan the Web, hoping to find open SSH devices and…
Vulnerability in Telegram allows to determine the user’s location
The Telegram messenger provides users with the People Nearby function, thanks to…
American special services named the target of the attack of Russian hackers
The Federal Bureau of Investigation (FBI), the US Cybersecurity and Infrastructure Protection…
Microsoft’s Windows Core Polaris OS build leaked online
A build of Windows Core Polaris for developers leaked online, confirming once…
Google Chrome conflict with anti viruses in Windows 10
In Google Chrome, we fixed a bug due to which antivirus programs…
The cyberattack on the United States turned out to be larger than anticipated
A cyberattack by "Russian hackers" on US government resources, which was first…
Ho.mobile Data Breach – Ho.Mobile Users Data are being Sold on Darknet
In the last days of 2020, rumors about the theft of data from…
Microsoft announced the penetration of hackers into the company’s internal networks
Microsoft has accused Russian hackers of taking over the source code of…