28 dangerous extensions detected for Google Chrome and Microsoft Edge
Avast experts have discovered malware hidden in at least 28 third-party extensions for Google…
Critical Infrastructure Warning! Millions of PLCs, switches, IoT devices are under threat
Eleven vulnerabilities, combined under the name Urgent / 11, were made public…
Why Is It Important To Have Intrusion Detection And Prevention ?
This article describes why detection and prevention of burglaries must be one…
The risk is real: attacks on OT infrastructure
Previously, many believed that attacks on an isolated OT infrastructure (Operational Technology)…
Gitpaste-12: Linux bot armed with a dozen exploits
Researchers at Juniper Networks have discovered a Linux scripting malware that has…
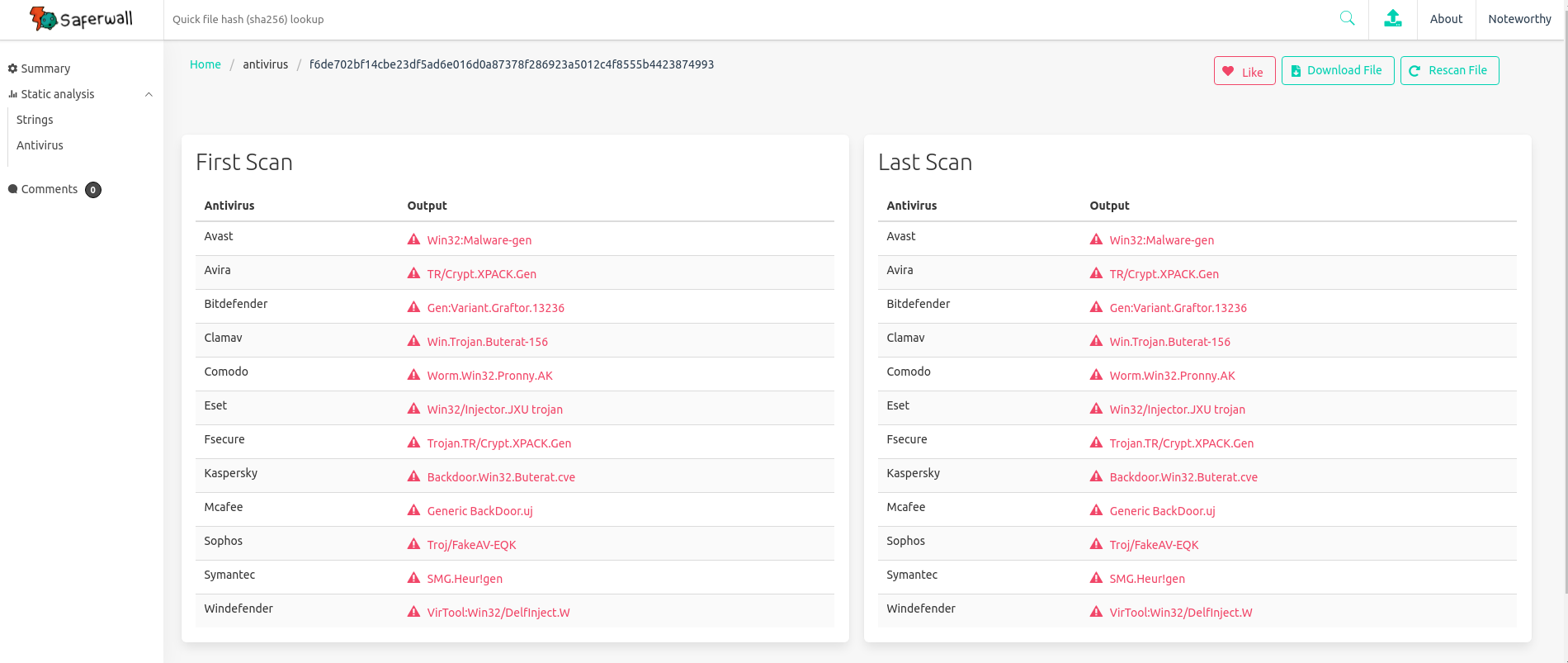
Saferwall : Open Source Malware Analysis
Saferwall is an open source malware analysis platform. It aims for the…
Network Vulnerability Assessment ? Why Should Every Company Do it at least once a Year !
Network vulnerability assessment analyzes a variety of network issues, prioritizes the most…
Artificial Intelligence and Cyber Security
As artificial intelligence intrudes into the world of cybersecurity, security analysts and…
Analysis of Windows Active Directory environment using BloodHound
This article examines the analysis of a Windows Active Directory environment using…