Check Point Detects Ransomware Spike on Healthcare Facilities Around the World
Trickbot and Emotet Trojans, Leading the Global Threat Index, Used to Spread…
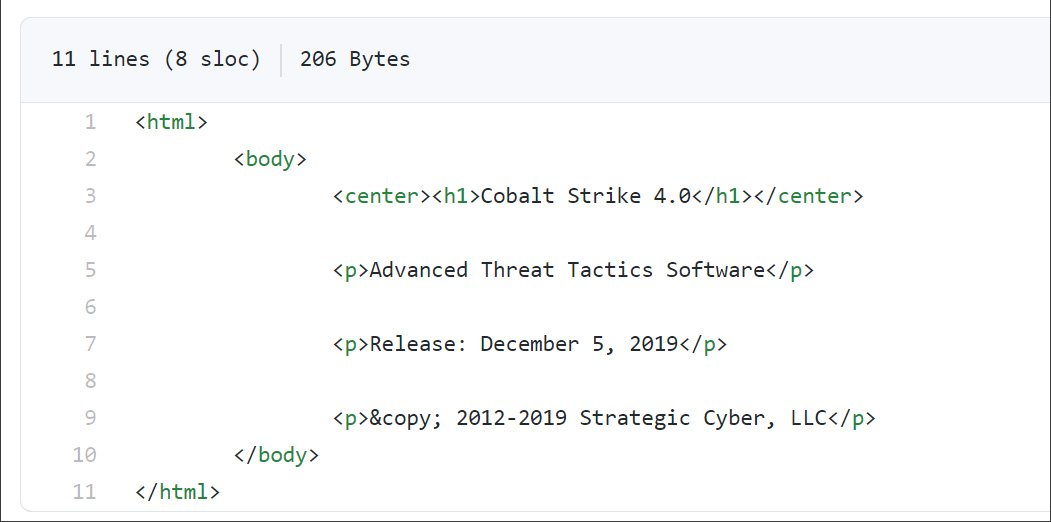
Cobalt Strike sources uploaded to GitHub
An open repository was found on GitHub, the contents of which are…
Comodo has published the EDR source code on GitHub
Comodo this week opened the source for its Endpoint Detection and Response…
Hacker Who Stole Personal Data for 100$ Million Teceived 8 years in Prison
Alexander Brovko, 36, received a sentence for stealing personal data and financial…
Guess who is on Telegram now? Magecart…
Criminal Hackers related to the Magecart collective are now using Telegram as a channel…
Threat Intelligence Automation
Cyber Threat Intelligence (CTI) is a framework and technology that generates intelligence…
OWASP – Open Web Application Security Project
The Open Web Application Security Project (OWASP) has compiled a list of…
Why Companies Should Care More About Credential Breach?
Phishing attacks and stolen credentials are becoming more common in the world…
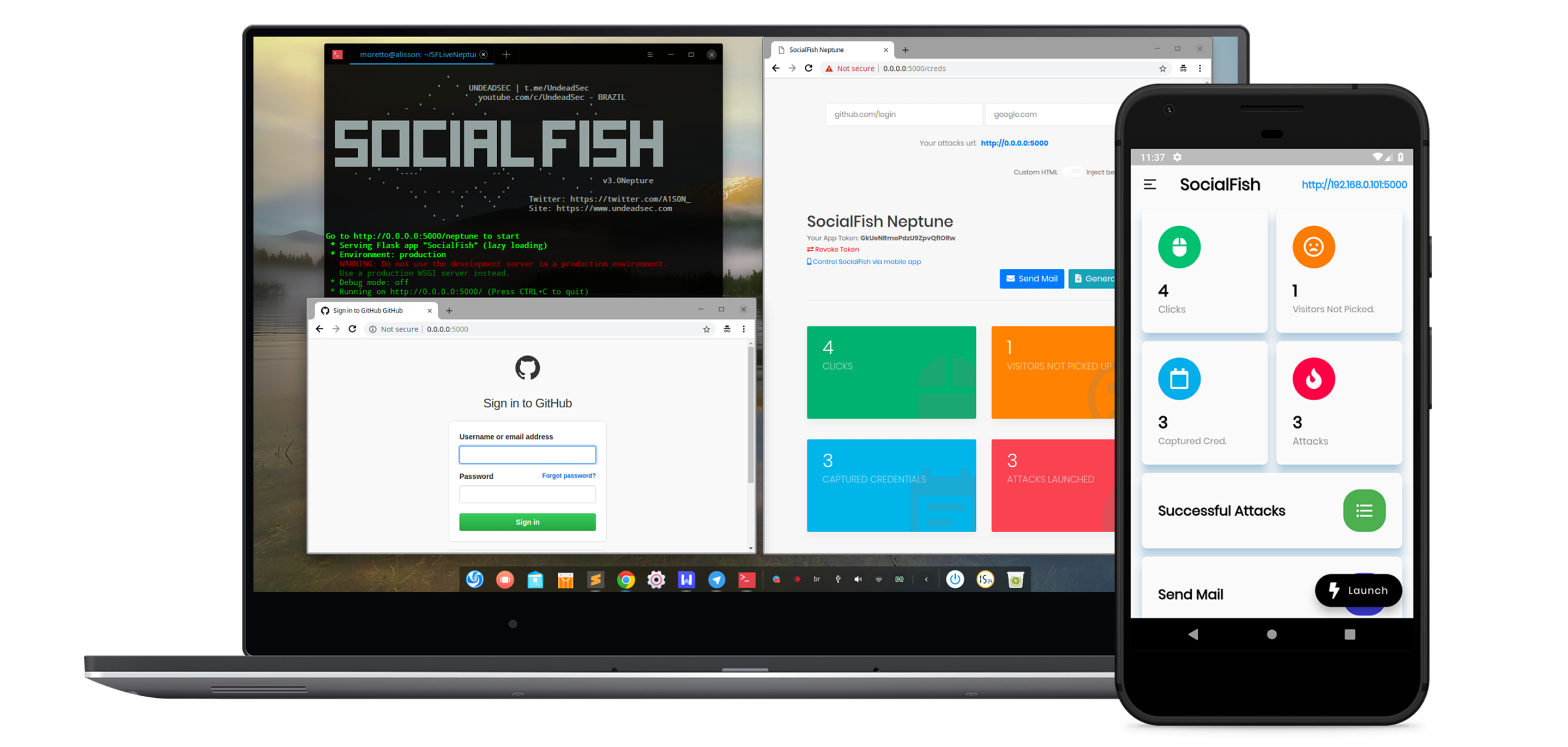
SocialFish – Let’s Go Phishing
SocialFish is an open-source phishing tool, integrated with another open source tool…
Astsu – A network scanner tool
A network scanner tool, developed in Python 3 using scapy. How it…