Several information security companies have published lists of SolarWinds customers who have been affected by the hacking of the company and the infection of the Orion platform with malware. The victims of hackers include tech companies, local governments, universities, hospitals, banks, telecom operators and many others.
Notable names include Cisco, SAP, Intel, Cox Communications, Deloitte, Nvidia, Fujitsu, Belkin, Amerisafe, Lukoil, Rakuten, Check Point, Optimizely, Digital Reach, and Digital Sense. MediaTek, one of the world’s largest semiconductor manufacturers, is also believed to have been affected, although researchers are not yet 100% sure.
Let me remind you that the malware that spread using malicious versions of Orion (released between March and June 2020) was codenamed SUNBURST (aka Solorigate). According to reports from Microsoft , FireEye , McAfee , Symantec , Kaspersky Lab and the US Department of Homeland Security’s Cybersecurity and Infrastructure Protection Agency ( DHS CISA ), the malware collected information about the victim’s network in infected systems, waited 12-14 days and then sent this data to the attackers’ remote server. If after that the malware operators recognized the company’s network as interesting, they developed the attack further and continued to collect information.
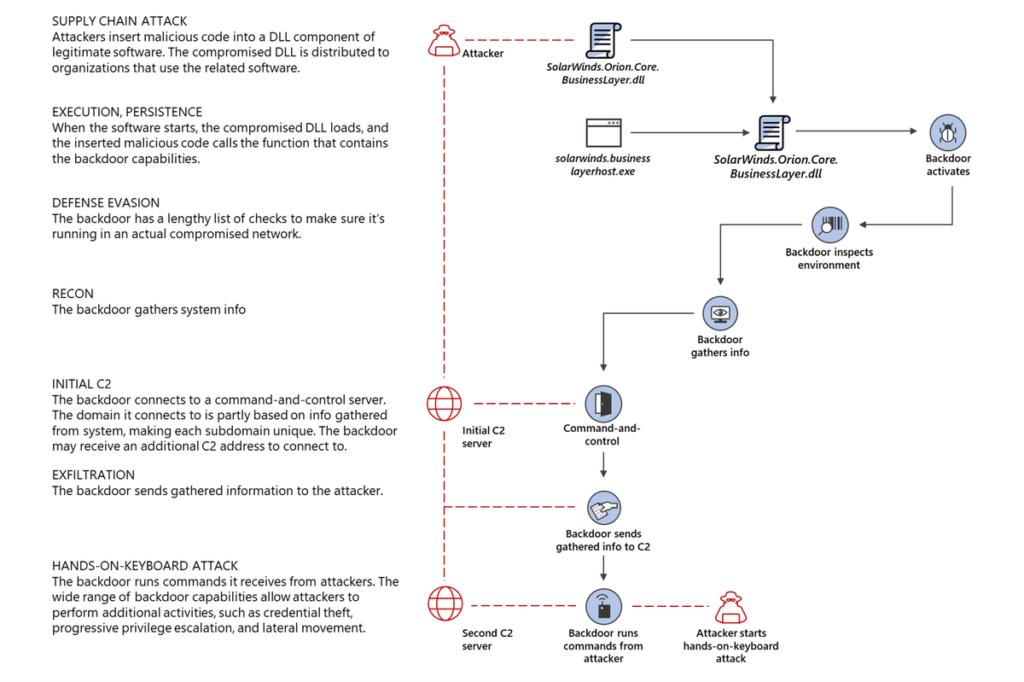
According to official figures, of the 300,000 SolarWinds customers, only 33,000 were using Orion, and the infected version of the platform was installed on 18,000 customers. Initially, it was believed that only SolarWinds specialists would be able to identify all the victims, but as other experts continued to study the work of SUNBURST, they discovered some peculiarities in the work of the malware. For example, related to how she pings her C&C server.
It turned out that SUNBURST was sending data collected on the infected network to the URL of its C&C server, unique for each victim. The unique URLs were subdomains of avsvmcloud [.] Com and consisted of four parts, the first of which was a seemingly random string. However, security researchers soon noticed that this string was not actually random, but contained the encoded domain name of the victim’s local network.
Let me remind you that, according to FireEye, despite the compromise of 18,000 SolarWinds customers, the hackers continued to attack only the networks of 50 companies . Microsoft experts, in turn, wrote that they were able to identify about 40 victims from among their customers.
The attack usually progressed when the avsvmcloud [.] Cxom control server responded to malware with a specific DNS response with a specific CNAME field. This special field contained the address of the second command and control server, from which SUNBURST could receive additional commands and sometimes download more malware.
At present, only one company is known for certain, which the hackers continued to hack – this is the information security company FireEye, whose reaction to the attack shed light on the compromise of SolarWinds in general.
Edition ZDNet reports that there are now many in the IB community work with content delivery networks, Internet service providers and other companies for the passive DNS data collection and tracking traffic avsvmcloud [.] Com. All this activity is aimed at identifying other victims, to whose networks cybercriminals could also gain in-depth access. Reporters cite a table compiled by the aforementioned company Truesec, which contains decoded internal domain names for some of the victims of the SolarWinds compromise. We quote this list below.
| Decoded internal name | Potential victim | Response address family | Team | First seen |
| mnh.rg-law.ac.il | College of Law and Business (Israel) | NetBios | HTTP Backdoor | 2020-05-26 |
| ad001.mtk.lo | Mediatek | NetBios | HTTP Backdoor | 2020-08-26 |
| Aeria | NetBios | HTTP Backdoor | 2020-06-26 | |
| Ameri | NetBios | HTTP Backdoor | 2020-08-02 | |
| ank.com | Ankcom Communications | NetBios | HTTP Backdoor | 2020-06-06 |
| azlcyy | NetBios | HTTP Backdoor | 2020-08-07 | |
| banccentral.com | BancCentral Financial Services Corp. | NetBios | HTTP Backdoor | 2020-07-03 |
| barrie.ca | Barrie City (Canada) | NetBios | HTTP Backdoor | 2020-05-13 |
| BCC.l | NetBios | HTTP Backdoor | 2020-08-22 | |
| bhq.lan | NetBios | HTTP Backdoor | 2020-08-18 | |
| cds.capilanou. | Capilano University (Canada) | NetBios | HTTP Backdoor | 2020-08-27 |
| Centr | NetBios | HTTP Backdoor | 2020-06-24 | |
| chc.dom | NetBios | HTTP Backdoor | 2020-08-04 | |
| christieclinic. | Christie Telemedicine Clinic | NetBios | HTTP Backdoor | 2020-04-22 |
| CIMBM | NetBios | HTTP Backdoor | 2020-09-25 | |
| CIRCU | NetBios | HTTP Backdoor | 2020-05-30 | |
| CONSO | NetBios | HTTP Backdoor | 2020-06-17 | |
| corp.ptci.com | Pioneer Telephone Scholarship Recipients | NetBios | HTTP Backdoor | 2020-06-19 |
| corp.stingraydi | Stingray | NetBios | HTTP Backdoor | 2020-06-10 |
| corp.stratusnet | Stratus Networks | NetBios | HTTP Backdoor | 2020-04-28 |
| cosgroves.local | Cosgroves | NetBios | HTTP Backdoor | 2020-08-25 |
| COTES | Cotes | NetBios | HTTP Backdoor | 2020-07-25 |
| csnt.princegeor | Prince George (Canada) | NetBios | HTTP Backdoor | 2020-09-18 |
| cys.local | CYS Group | NetBios | HTTP Backdoor | 2020-07-10 |
| digitalsense.co | Digital sense | NetBios | HTTP Backdoor | 2020-06-24 |
| ehtuh- | NetBios | HTTP Backdoor | 2020-05-01 | |
| escap.org | NetBios | HTTP Backdoor | 2020-07-10 | |
| f.gnam | NetBios | HTTP Backdoor | 2020-04-04 | |
| fhc.local | NetBios | HTTP Backdoor | 2020-07-06 | |
| fidelitycomm.lo | Fidelity Communications | NetBios | HTTP Backdoor | 2020-06-02 |
| fisherbartoninc.com | The Fisher Barton Group | NetBios | HTTP Backdoor | 2020-05-15 |
| fmtn.ad | Farmington town | NetBios | HTTP Backdoor | 2020-07-21 |
| FWO.I | NetBios | HTTP Backdoor | 2020-08-05 | |
| ggsg-us.cisco | Cisco GGSG | NetBios | HTTP Backdoor | 2020-06-24 |
| ghsmain1.ggh.g | NetBios | HTTP Backdoor | 2020-06-09 | |
| gxw | NetBios | HTTP Backdoor | 2020-07-07 | |
| htwanmgmt.local | NetBios | HTTP Backdoor | 2020-07-22 | |
| ieb.go.id | NetBios | HTTP Backdoor | 2020-06-12 | |
| int.ncahs.net | NetBios | HTTP Backdoor | 2020-09-23 | |
| internal.jtl.c | NetBios | HTTP Backdoor | 2020-05-19 | |
| ironform.com | Ironform | NetBios | HTTP Backdoor | 2020-06-19 |
| isi | NetBios | HTTP Backdoor | 2020-07-06 | |
| itps.uk.net | Infection Prevention Society | NetBios | HTTP Backdoor | 2020-08-11 |
| jxxyx. | NetBios | HTTP Backdoor | 2020-06-26 | |
| kcpl.com | Kansas City Power and Light Company | NetBios | HTTP Backdoor | 2020-07-07 |
| keyano.local | Kiano College | NetBios | HTTP Backdoor | 2020-06-03 |
| khi0kl | NetBios | HTTP Backdoor | 2020-08-26 | |
| lhc_2f | NetBios | HTTP Backdoor | 2020-04-18 | |
| lufkintexas.net | Lufkin City (Texas, USA) | NetBios | HTTP Backdoor | 2020-07-07 |
| magnoliaisd.loc | Magnolia Independent School District | NetBios | HTTP Backdoor | 2020-06-01 |
| MOC.l | NetBios | HTTP Backdoor | 2020-04-30 | |
| moncton.loc | Moncton City (Canada) | NetBios | HTTP Backdoor | 2020-08-25 |
| mountsinai.hosp | Mount Sinai Hospital | NetBios | HTTP Backdoor | 2020-07-02 |
| netdecisions.lo | Netdecisions | NetBios | HTTP Backdoor | 2020-10-04 |
| newdirections.k | NetBios | HTTP Backdoor | 2020-04-21 | |
| nswhealth.net | NSW Health | NetBios | HTTP Backdoor | 2020-06-12 |
| nzi_9p | NetBios | HTTP Backdoor | 2020-08-04 | |
| city.kingston.on.ca | City of Kingston (Canada) | NetBios | HTTP Backdoor | 2020-06-15 |
| dufferincounty.on.ca | Dufferin County (Canada) | NetBios | HTTP Backdoor | 2020-07-17 |
| osb.local | NetBios | HTTP Backdoor | 2020-04-28 | |
| oslerhc.org | William Osler Health System | NetBios | HTTP Backdoor | 2020-07-11 |
| pageaz.gov | City of Page (USA) | NetBios | HTTP Backdoor | 2020-04-19 |
| pcsco.com | Professional Computer Systems | NetBios | HTTP Backdoor | 2020-07-23 |
| pkgix_ | NetBios | HTTP Backdoor | 2020-07-15 | |
| pqcorp.com | PQ Corporation | NetBios | HTTP Backdoor | 2020-07-02 |
| prod.hamilton. | Hamilton company | NetBios | HTTP Backdoor | 2020-08-19 |
| resprod.com | Res Group | NetBios | HTTP Backdoor | 2020-05-06 |
| RPM.l | NetBios | HTTP Backdoor | 2020-05-28 | |
| sdch.local | South Davis Community Hospital | NetBios | HTTP Backdoor | 2020-05-18 |
| servitia.intern | NetBios | HTTP Backdoor | 2020-06-16 | |
| sfsi.stearnsban | Bank Stearns | NetBios | HTTP Backdoor | 2020-08-02 |
| signaturebank.l | Signature Bank | NetBios | HTTP Backdoor | 2020-06-25 |
| sm-group.local | SM Group | NetBios | HTTP Backdoor | 2020-07-07 |
| te.nz | TE Connectivity | NetBios | HTTP Backdoor | 2020-05-13 |
| thx8xb | NetBios | HTTP Backdoor | 2020-06-16 | |
| tx.org | NetBios | HTTP Backdoor | 2020-07-15 | |
| usd373.org | Newton Public Schools | NetBios | HTTP Backdoor | 2020-08-01 |
| uzq | NetBios | HTTP Backdoor | 2020-10-02 | |
| ville.terrebonn | Ville de terrebonne | NetBios | HTTP Backdoor | 2020-08-02 |
| wrbaustralia.ad | WR Berkley Insurance Australia | NetBios | HTTP Backdoor | 2020-07-11 |
| ykz | NetBios | HTTP Backdoor | 2020-07-11 | |
| 2iqzth | ImpLink | Enum processes | 2020-06-17 | |
| 3if.2l | 3IF | ImpLink | Enum processes | 2020-08-20 |
| airquality.org | Sacramento Metropolitan Air Quality Management District | ImpLink | Enum processes | 2020-08-09 |
| ansc.gob.pe | GOB | ImpLink | Enum processes | 2020-07-25 |
| bcofsa.com.ar | Banco de Formosa | ImpLink | Enum processes | 2020-07-13 |
| bi.corp | ImpLink | Enum processes | 2020-12-14 | |
| bop.com.pk | The Bank of Punjab | ImpLink | Enum processes | 2020-09-18 |
| camcity.local | ImpLink | Enum processes | 2020-08-07 | |
| cow.local | ImpLink | Enum processes | 2020-06-13 | |
| deniz.denizbank | DenizBank | ImpLink | Enum processes | 2020-11-14 |
| ies.com | IES Communications | ImpLink | Enum processes | 2020-06-11 |
| insead.org | INSEAD Business School | ImpLink | Enum processes | 2020-11-07 |
| KS.LO | ImpLink | Enum processes | 2020-07-10 | |
| mixonhill.com | Mixon hill | ImpLink | Enum processes | 2020-04-29 |
| ni.corp.natins | ImpLink | Enum processes | 2020-10-24 | |
| phabahamas.org | Public Health Administration (Caribbean) Caribbean | ImpLink | Enum processes | 2020-11-05 |
| rbe.sk.ca | Regina Public Schools (Canada) | ImpLink | Enum processes | 2020-08-20 |
| spsd.sk.ca | Saskatoon Public Schools (Canada) | ImpLink | Enum processes | 2020-06-12 |
| yorkton.cofy | Community Options for Families & Youth | ImpLink | Enum processes | 2020-05-08 |
| .sutmf | Ipx | Update config | 2020-06-25 | |
| atg.local | No Match | Unknown | 2020-05-11 | |
| bisco.int | Bisco International | No Match | Unknown | 2020-04-30 |
| ccscurriculum.c | No Match | Unknown | 2020-04-18 | |
| e-idsolutions. | IDSolutions | No Match | Unknown | 2020-07-16 |
| ETC1. | No Match | Unknown | 2020-08-01 | |
| gk5 | No Match | Unknown | 2020-07-09 | |
| grupobazar.loca | No Match | Unknown | 2020-06-07 | |
| internal.hws.o | No Match | Unknown | 2020-05-23 | |
| n2k | No Match | Unknown | 2020-07-12 | |
| publiser.it | No Match | Unknown | 2020-07-05 | |
| us.deloitte.co | Deloitte | No Match | Unknown | 2020-07-08 |
| ush.com | No Match | Unknown | 2020-06-15 | |
| xijtt- | No Match | Unknown | 2020-07-21 | |
| xnet.kz | X NET | No Match | Unknown | 2020-06-09 |
| zu0 | No Match | Unknown | 2020-08-13 | |
| staff.technion.ac.il | N / A | N / A | N / A | |
| digitalreachinc.com | N / A | N / A | N / A | |
| orient-express.com | N / A | N / A | N / A | |
| tr.technion.ac.il | N / A | N / A | N / A | |
| lasers.state.la.us | N / A | N / A | N / A | |
| ABLE. | N / A | N / A | N / A | |
| abmuh_ | N / A | N / A | N / A | |
| acmedctr.ad | N / A | N / A | N / A | |
| ad.azarthritis.com | N / A | N / A | N / A | |
| ad.library.ucla.edu | N / A | N / A | N / A | |
| ad.optimizely. | N / A | N / A | N / A | |
| admin.callidusc | N / A | N / A | N / A | |
| aerioncorp.com | N / A | N / A | N / A | |
| agloan.ads | N / A | N / A | N / A | |
| ah.org | N / A | N / A | N / A | |
| AHCCC | N / A | N / A | N / A | |
| allegronet.co. | N / A | N / A | N / A | |
| alm.brand.dk | N / A | N / A | N / A | |
| amalfi.local | N / A | N / A | N / A | |
| americas.phoeni | N / A | N / A | N / A | |
| amr.corp.intel | N / A | N / A | N / A | |
| apu.mn | N / A | N / A | N / A | |
| ARYZT | N / A | N / A | N / A | |
| b9f9hq | N / A | N / A | N / A | |
| BE.AJ | N / A | N / A | N / A | |
| belkin.com | N / A | N / A | N / A | |
| bk.local | N / A | N / A | N / A | |
| bmrn.com | N / A | N / A | N / A | |
| bok.com | N / A | N / A | N / A | |
| btb.az | N / A | N / A | N / A | |
| c4e-internal.c | N / A | N / A | N / A | |
| calsb.org | N / A | N / A | N / A | |
| casino.prv | N / A | N / A | N / A | |
| cda.corp | N / A | N / A | N / A | |
| central.pima.g | N / A | N / A | N / A | |
| cfsi.local | N / A | N / A | N / A | |
| ch.local | N / A | N / A | N / A | |
| ci.dublin.ca. | N / A | N / A | N / A | |
| cisco.com | N / A | N / A | N / A | |
| corp.dvd.com | N / A | N / A | N / A | |
| corp.sana.com | N / A | N / A | N / A | |
| Count | N / A | N / A | N / A | |
| COWI. | N / A | N / A | N / A | |
| coxnet.cox.com | N / A | N / A | N / A | |
| CRIHB | N / A | N / A | N / A | |
| cs.haystax.loc | N / A | N / A | N / A | |
| csa.local | N / A | N / A | N / A | |
| csci-va.com | N / A | N / A | N / A | |
| csqsxh | N / A | N / A | N / A | |
| DCCAT | N / A | N / A | N / A | |
| deltads.ent | N / A | N / A | N / A | |
| detmir-group.r | N / A | N / A | N / A | |
| dhhs- | N / A | N / A | N / A | |
| dmv.state.nv. | N / A | N / A | N / A | |
| dotcomm.org | N / A | N / A | N / A | |
| DPCIT | N / A | N / A | N / A | |
| dskb2x | N / A | N / A | N / A | |
| e9.2pz | N / A | N / A | N / A | |
| ebe.co.roanoke.va.us | N / A | N / A | N / A | |
| ecobank.group | N / A | N / A | N / A | |
| ecocorp.local | N / A | N / A | N / A | |
| epl.com | N / A | N / A | N / A | |
| fremont.lamrc. | N / A | N / A | N / A | |
| FSAR. | N / A | N / A | N / A | |
| ftfcu.corp | N / A | N / A | N / A | |
| gksm.local | N / A | N / A | N / A | |
| gloucesterva.ne | N / A | N / A | N / A | |
| glu.com | N / A | N / A | N / A | |
| gnb.local | N / A | N / A | N / A | |
| gncu.local | N / A | N / A | N / A | |
| gsf.cc | N / A | N / A | N / A | |
| gyldendal.local | N / A | N / A | N / A | |
| helixwater.org | N / A | N / A | N / A | |
| hgvc.com | N / A | N / A | N / A | |
| ia.com | N / A | N / A | N / A | |
| inf.dc.net | N / A | N / A | N / A | |
| ingo.kg | N / A | N / A | N / A | |
| innout.corp | N / A | N / A | N / A | |
| int.lukoil-international.uz | N / A | N / A | N / A | |
| intensive.int | N / A | N / A | N / A | |
| ions.com | N / A | N / A | N / A | |
| its.iastate.ed | N / A | N / A | N / A | |
| jarvis.lab | N / A | N / A | N / A | |
| -jlowd | N / A | N / A | N / A | |
| jn05n8 | N / A | N / A | N / A | |
| jxb3eh | N / A | N / A | N / A | |
| k.com | N / A | N / A | N / A | |
| LABEL | N / A | N / A | N / A | |
| milledgeville.l | N / A | N / A | N / A | |
| nacr.com | N / A | N / A | N / A | |
| ncpa.loc | N / A | N / A | N / A | |
| neophotonics.co | N / A | N / A | N / A | |
| net.vestfor.dk | N / A | N / A | N / A | |
| nih.if | N / A | N / A | N / A | |
| nvidia.com | N / A | N / A | N / A | |
| on-pot | N / A | N / A | N / A | |
| ou0yoy | N / A | N / A | N / A | |
| paloverde.local | N / A | N / A | N / A | |
| pl8uw0 | N / A | N / A | N / A | |
| q9owtt | N / A | N / A | N / A | |
| rai.com | N / A | N / A | N / A | |
| rccf.ru | N / A | N / A | N / A | |
| repsrv.com | N / A | N / A | N / A | |
| ripta.com | N / A | N / A | N / A | |
| roymerlin.com | N / A | N / A | N / A | |
| rs.local | N / A | N / A | N / A | |
| rst.atlantis-pak.ru | N / A | N / A | N / A | |
| sbywx3 | N / A | N / A | N / A | |
| sc.pima.gov | N / A | N / A | N / A | |
| scif.com | N / A | N / A | N / A | |
| SCMRI | N / A | N / A | N / A | |
| scroot.com | N / A | N / A | N / A | |
| seattle.interna | N / A | N / A | N / A | |
| securview.local | N / A | N / A | N / A | |
| SFBAL | N / A | N / A | N / A | |
| SF-Li | N / A | N / A | N / A | |
| siskiyous.edu | N / A | N / A | N / A | |
| sjhsagov.org | N / A | N / A | N / A | |
| Smart | N / A | N / A | N / A | |
| smes.org | N / A | N / A | N / A | |
| sos-ad.state.nv.us | N / A | N / A | N / A | |
| sro.vestfor.dk | N / A | N / A | N / A | |
| superior.local | N / A | N / A | N / A | |
| swd.local | N / A | N / A | N / A | |
| ta.org | N / A | N / A | N / A | |
| taylorfarms.com | N / A | N / A | N / A | |
| thajxq | N / A | N / A | N / A | |
| thoughtspot.int | N / A | N / A | N / A | |
| tsyahr | N / A | N / A | N / A | |
| tv2.local | N / A | N / A | N / A | |
| uis.kent.edu | N / A | N / A | N / A | |
| uncity.dk | N / A | N / A | N / A | |
| uont.com | N / A | N / A | N / A | |
| viam-invenient | N / A | N / A | N / A | |
| vms.ad.varian.com | N / A | N / A | N / A | |
| vsp.com | N / A | N / A | N / A | |
| WASHO | N / A | N / A | N / A | |
| weioffice.com | N / A | N / A | N / A | |
| wfhf1.hewlett. | N / A | N / A | N / A | |
| woodruff-sawyer | N / A | N / A | N / A | |
| HQ.RE-wwgi2xnl | N / A | N / A | N / A | |
| xdxinc.net | N / A | N / A | N / A | |
| y9k.in | N / A | N / A | N / A | |
| zeb.i8 | N / A | N / A | N / A | |
| zippertubing.co | N / A | N / A | N / A |





