Exploit in Microsoft Teams Allows Bypassing Restrictions on Incoming Files
US Navy red team member Alex Reid has created the TeamsPhisher tool, which exploits an issue in Microsoft Teams to bypass restrictions on incoming files received from users outside of the target organization.
TeamsPhisher was created on the basis of a study by the information security company Jumpsec, published at the end of June. At that time, experts wrote that an attacker could easily bypass Microsoft Teams restrictions on sending files and use this problem to deliver malware.
The point is that existing client-side security can be easily fooled into forcing Microsoft Teams to treat an external user as an internal user. And for this, it is enough just to change the ID in the POST request.
Written in Python, TeamsPhisher combines the concept of an attack proposed by Jumpsec, as well as methods developed by information security expert Andrea Santese and a number of features of the TeamsEnum tool.
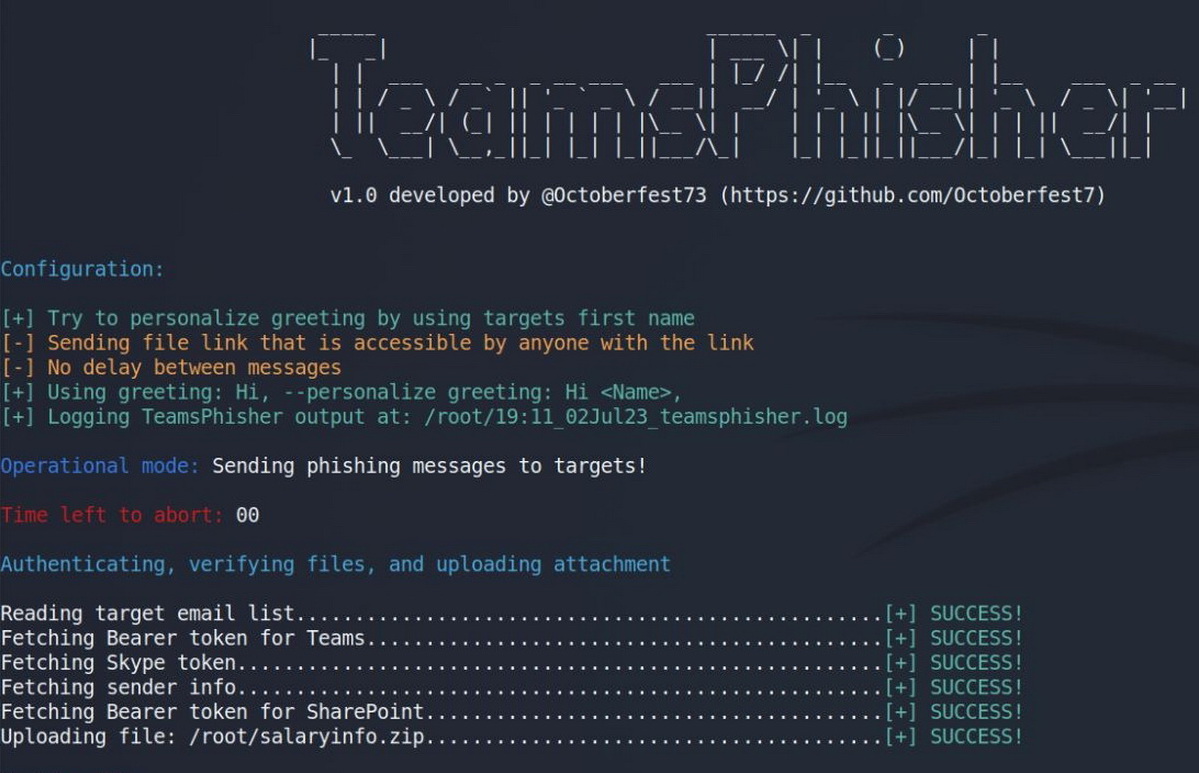
“Give TeamsPhisher an attachment, a message, and a list of target Teams users. It will upload the attachment to the sender’s Sharepoint and then iterate through the list of targets,” writes Alex Reed.
How Does TeamsPhisher Work?
TeamsPhisher first checks whether the target user exists and can receive external messages (this is a prerequisite for the attack to be carried out). It then creates a new thread with the target and sends a message with a link to the attachment in Sharepoint. The thread appears in the sender’s Teams interface and can be interacted with manually.
For a successful attack, TeamsPhisher requires the user to have a Microsoft Business account with a valid Teams and Sharepoint license, which is typical for many large companies.
In addition, TeamsPhisher has a number of features that will help improve the attack. These include sending secure links to files (which can only be viewed by a specific recipient), setting a delay on sending messages (to bypass rate limits), and logging output.
Microsoft’s Response to the Issue
The problem discovered last month by Jumpsec specialists, and now used by TeamsPhisher, is still relevant. Microsoft developers reported that this bug does not require an immediate fix.
Bleeping Computer publishes Microsoft’s commentary on this error. The company said that the success of such attacks depends entirely on social engineering, and advised customers to follow the basic rules of “digital hygiene”, that is, “be careful when clicking on links to web pages, opening unknown files or accepting file transfers.”