Experts have discovered a new phishing-as-a-service platform called Greatness. Since mid-2022, the platform has been used to target business users of Microsoft 365 cloud services, significantly lowering the entry threshold for phishers.
According to Cisco Talos, Greatness specializes in phishing pages for Microsoft 365, providing customers with attachments and a link builder that enables them to create “highly convincing bait and landing pages.” Features such as pre-populating the victim’s email address, displaying the appropriate company logo, and a background image extracted from the actual Microsoft 365 sign-in page for the target organization are included.
Greatness campaigns have primarily targeted manufacturing, medical, and technology organizations in the US, UK, Australia, South Africa, and Canada. Bursts of such attacks were recorded in December 2022 and March 2023.
Phishing attacks begin with malicious emails containing HTML attachments that execute obfuscated JavaScript code when opened. This redirects the user to a landing page pre-populated with their email address, where they are asked for a password and multi-factor authentication code.
All entered data and tokens are then sent to the attackers’ Telegram channel, giving them the opportunity to gain unauthorized access to compromised accounts.
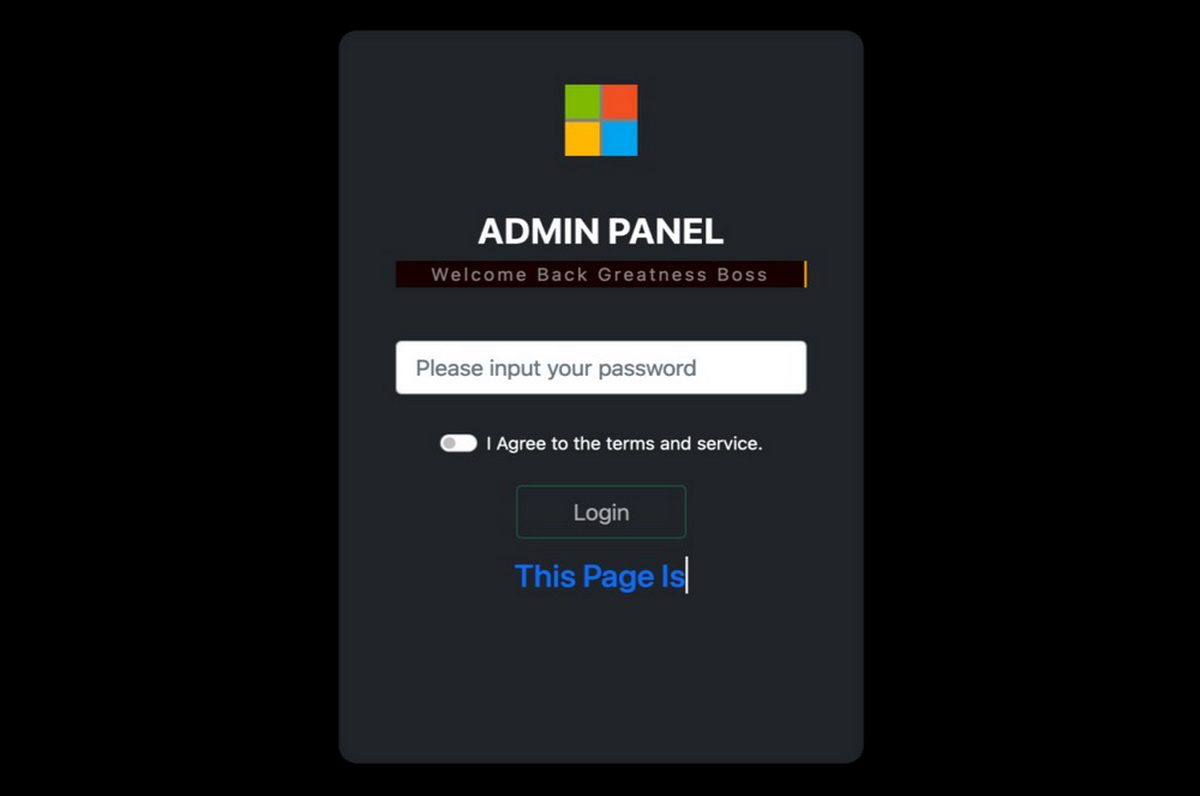
Phishers are also provided with an administration panel that allows them to set up a Telegram bot, track stolen information, and create custom attachments or trap links.
In addition, each client must have a valid API key to be able to download the phishing page. The API key also prevents browsing to a phishing page from unwanted IP addresses and makes it easier to hide from the real Microsoft 365 sign-in page.