Analysts at McAfee found five extensions for Google Chrome in the Chrome Web Store that were fraudulent with user data. Specifically, the extensions tracked when users visited certain e-commerce sites and modified cookies to make it look like the user had followed a referral link.
The five extensions, with a total of over 1.4 million downloads, were named as follows:
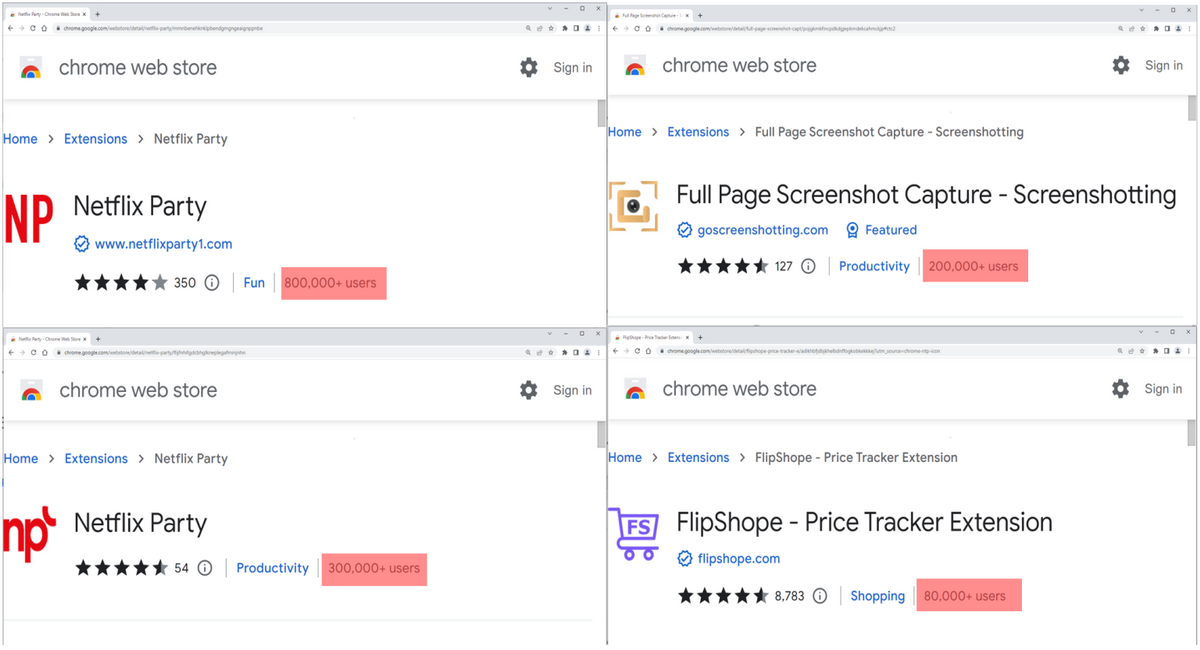
- Netflix Party (mmnbenehknklpbendgmgngeaignppnbe) – 800,000 installs;
- (mmnbenehknklpbendgmgngeaignppnbe) – 800,000 installs; Netflix Party 2 (flijfnhifgdcbhglkneplegafminjnhn) – 300,000 installs;
- (flijfnhifgdcbhglkneplegafminjnhn) – 300,000 installs; Full Page Screenshot Capture – Screenshotting (pojgkmkfincpdgjepkmdekcahmckjp) – 200,000 installs;
- (pojgkmkfincpdkdgjepkmdekcahmckjp) – 200,000 installs; FlipShope – Price Tracker Extension (adikhbfjdbjkhelbdnffogkobkekkkej) – 80,000 installs;
- (adikhbfjdbjkhelbdnffogkobkekkkej) — 80,000 installs; AutoBuy Flash Sales (gbnahglfafmhaehbdmjedfhdmimjcbed) — 20,000 installs.
It is noted that all extensions really had the declared functionality, which made it harder for victims to notice their malicious activity.
The researchers write that the use of these extensions did not directly affect users, but these products still posed a serious threat to privacy. According to analysts, all five extensions acted in the same way: the application manifest (manifest.json file), which defines the behavior of the extension in the system, loaded a rich script (B0.js), which transmitted browsing data to a domain controlled by attackers (langhort[.]com ).
The data was passed through POST requests, and this happened every time the user visited a new URL. The information that the scammers eventually received included the URL itself in base64 format, the user ID, the location of the device (country, city, postal code). cs) and an encoded referral URL.
If the resource visited by the victim matched the entries in a special list of sites with which the authors of the malware are associated, the server responded with B0.js as follows. In the first case, the command Result[‘c’] – passf_url told the script to insert the provided URL (referral link) into the site as an iframe. In the second case, Result[‘e’] setCookie told B0.js to change the cookie or replace it with the provided one (if the extension had the rights to do so). McAfee posted a video demonstrating how these URL and cookie spoofs happened.
To avoid detection, complicate analysis, and confuse security researchers and vigilant users, some of the extensions began fraudulent activity at least 15 days after installation.
Currently, all extensions have already been removed from the Chrome Web Store, but this does not mean they are removed from users’ browsers. The victims will have to get rid of the extensions manually.