Kaspersky Lab experts have discovered a hard-to-detect SessionManager backdoor that allows access to corporate IT infrastructure and perform a wide range of malicious actions. So, the malware can read corporate mail, distribute other malware, and remotely control infected servers.
Analysts say that attackers inject malware remotely, as a module for Microsoft IIS (a set of web services that includes the Exchange mail server). To spread SessionManager and other malicious IIS modules, hackers exploit the well-known ProxyLogon vulnerability .
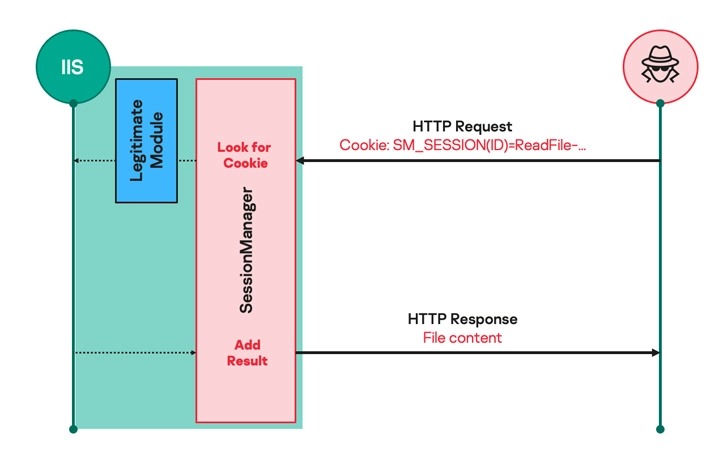
“Using the IIS module as a backdoor allows attackers to maintain persistent, update-resistant, and relatively stealthy access to the target organization’s IT infrastructure; whether it’s harvesting emails, updating further malicious access, or covertly managing compromised servers that can be used as a malicious infrastructure,” the company’s report reads.
According to Kaspersky Lab, the first attacks using the SessionManager were recorded at the end of March 2021. The victims of hackers were predominantly government agencies and non-profit organizations in Africa, South Asia, Europe and the Middle East, as well as in Russia.
So far, the backdoor has been found on 34 servers in 24 companies. But the report notes that the SessionManager often goes unnoticed, as it is poorly detected by most popular online crawlers.
Analysts say these attacks are most likely related to the Gelsemium group , citing similarities in malware samples as well as similar targets.
“Became publicly known in early 2021, the ProxyLogon vulnerability in the Microsoft Exchange server gave attackers a new vector for attacks that they actively use, including for downloading backdoors in the form of IIS web server modules. With the help of one of these malware, SessionManager, attackers gain update-resistant, long-term and successfully hidden access to corporate IT infrastructure,” says Denis Legezo, a leading cybersecurity expert at Kaspersky Lab.





