Cisco Talos experts have discovered the ZingoStealer malware, which is distributed for free by the Haskers Gang hacker group.
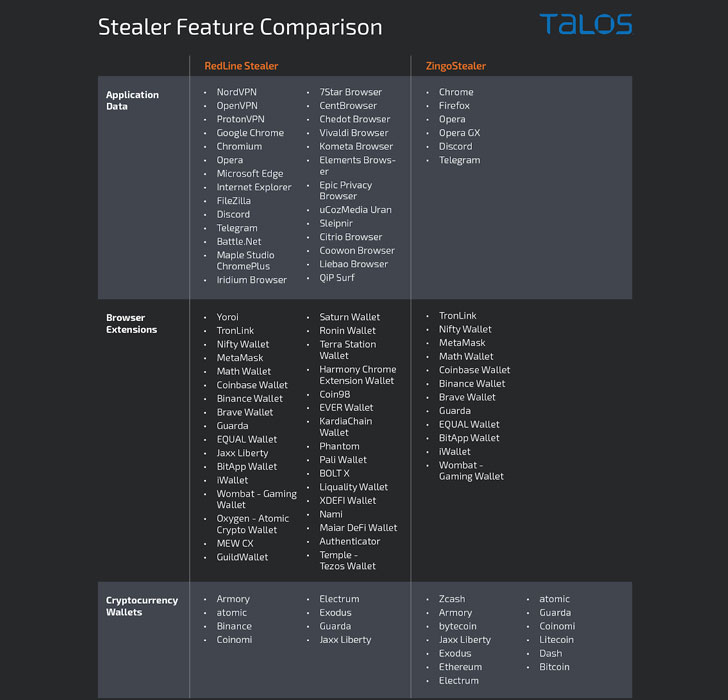
The malware is capable of stealing confidential information and uploading additional malware to infected systems. For example, it can be RedLine Stealer and XMRig-based cryptocurrency mining malware called ZingoMiner.
Haskers Gang has been active since at least January 2020, while ZingoStealer came out around the last month, according to analysts. Experts say the malware is constantly evolving and is mainly aimed at Russian-speaking victims, spreading mainly through game cheats and pirated software. For example, attackers post videos on YouTube advertising such tools, and add links to files hosted on Google Drive or Mega, which contain the ZingoStealer payload, in the description.
Cisco Talos also says that malware executables have been spotted on the Discord CDN, raising the possibility that the malware is spreading to game-related Discord servers as well.
In addition to collecting sensitive information such as credentials, cryptocurrency wallet information, and mining on victim systems, ZingoStealer is known to use Telegram to extract data and distribute updates. In addition, customers can pay about $3 to use the ExoCrypt cryptor, which allows you to bypass anti-virus protection.
At the same time, the report emphasizes that last week the Haskers Gang even announced that it was transferring ownership of ZingoStealer to another attacker, and also offered to sell the source code for a negotiated price of approximately $500.