The experts warned that attackers are already actively scanning the network in search of VMware vCenter servers vulnerable to the recently fixed critical RCE issue CVE-2021-21985, which scored 9.8 out of 10 on the CVSS v3 vulnerability rating scale.
Analysts of the Bad Packets company, as well as the well-known information security expert Kevin Beaumont, write about the scans that have begun.
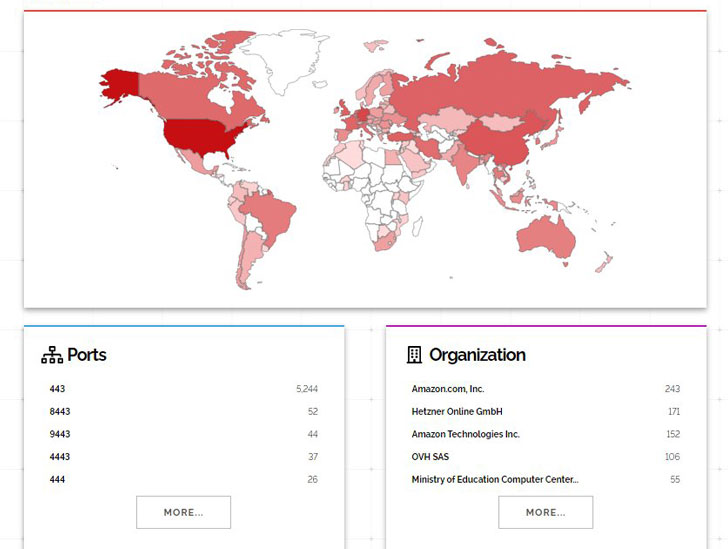
According to the search engine Shodan, there are currently several thousand vulnerable vCenter servers on the network. And you need to understand that this product is not used by individuals and even small businesses, that is, we are talking about large companies and organizations.
As a reminder, the CVE-2021-21985 issue was detected in the Virtual SAN Health Check plugin included by default with vCenter. An attacker can use this bug to run whatever they want on a vulnerable host (provided they can access port 443). That is, unauthenticated attackers can exploit the problem, and such attacks do not require any interaction with the user.
Even worse, exploits for this bug have already been published online .
Since such vulnerabilities have been used more than once in the past for destructive attacks (usually ransomware) against large companies, VMware representatives issued an official warning to their customers. In a statement, the company calls for timely installation of updates, as well as being on the alert and wary of ransomware attacks:
“In the era of ransomware, the safest thing to do is to assume that an attacker is already somewhere on the network, on the desktop, or perhaps already in control of a user account. Therefore, we strongly recommend that you install the emergency updates and patches as soon as possible. “