Forescout experts presented a report on nine vulnerabilities in TCP / IP stacks, collectively named NAME: WRECK . These problems affect hundreds of millions of servers, smart devices, and industrial equipment.
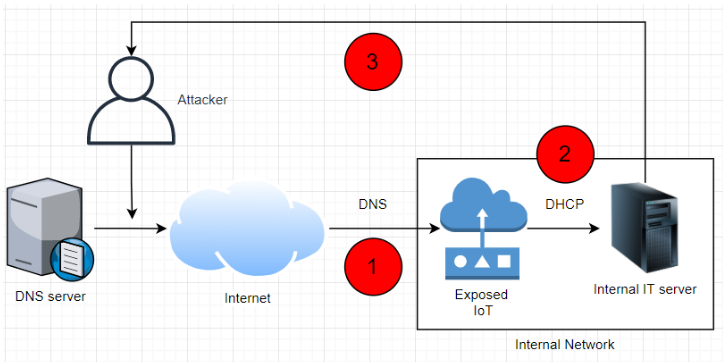
NAME: WRECK is the fifth set of vulnerabilities affecting TCP / IP libraries found in the past three years. Suffice it to recall at least such “findings” of experts as Ripple20 , URGENT / 11 and Amnesia: 33 . But all of the previous research looked at various TCP / IP mechanisms, and the NAME: WRECK study focuses on how libraries handle DNS traffic.
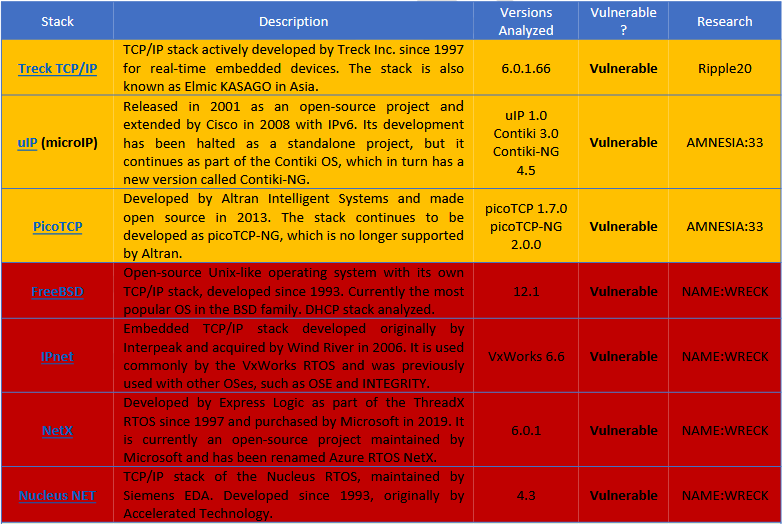
Forescout experts write that they found a total of nine vulnerabilities affecting 7 out of 15 TCP / IP stacks. Thus, three stacks are vulnerable to errors related to compression of DNS messages found in previous studies (such as Ripple 20 and Amnesia: 33), and four more stacks are vulnerable to new bugs found during the new analysis.
Among the other eight FNET libraries studied, cycloneTCP, uC / TCP-IP, FreeRTOS + TCP, Zephyr and OpenThread safely implement message compression, while Nut / Net and lwIP do not support message compression in principle, that is, they cannot be vulnerable.
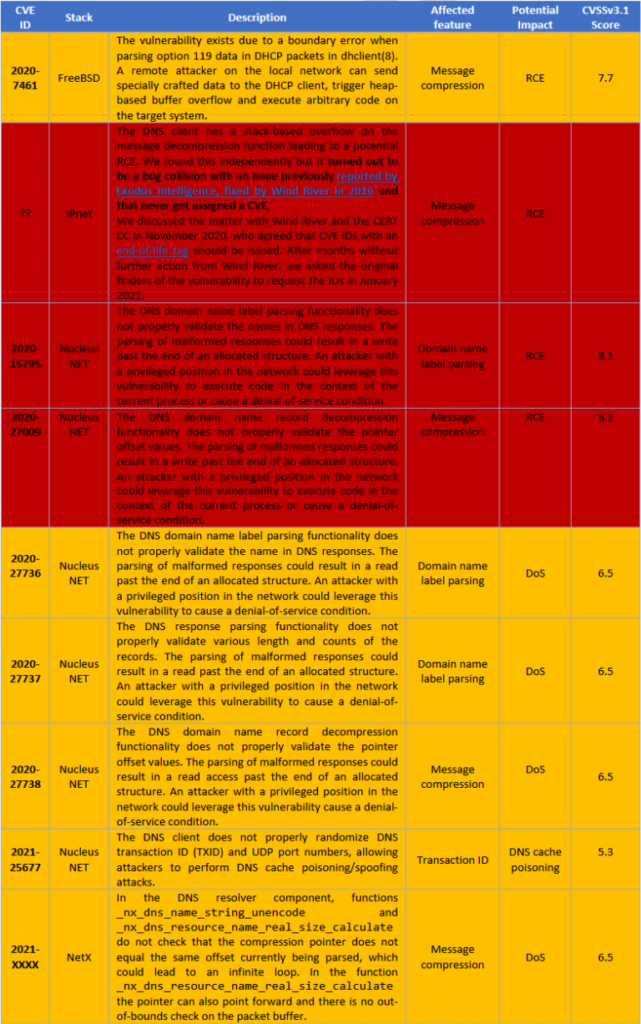
It is reported that so far only developers of 3 out of 4 vulnerable stacks have released patches: patches were prepared by FreeBSD, Nucleus NET and NetX, and the creators of IPNet are still working on solving the problems.
While the release of fixes is great, the researchers warn that the situation is actually far from ideal. The fact is that installing patches on smart devices and industrial equipment usually takes a long time, since for this device manufacturers must integrate patches with their code and release their own firmware updates. Then these updates must be installed by clients, which can also become a problem, because many devices are installed in remote locations and are difficult to access without the firmware update mechanism “over the air” (FOTA), which is not supported by all devices.
Worse, only a few of the NAME: WRECK vulnerabilities require an attacker to be able to tamper with the victim’s DNS traffic. Edition of The the Record , communicate with researchers, he says that there are other vulnerabilities that can be used for the organization of remote attacks: an attacker would be enough to bombard vulnerable systems distorted DNS responses.