Astsu – A network scanner tool
A network scanner tool, developed in Python 3 using scapy. How it…
Elasticsearch Data Breach – Genealogy Software Maker Exposes Data on 60,000 Users
A US tech company that manages popular family tree software has exposed…
Artificial Intelligence and Cyber Security
As artificial intelligence intrudes into the world of cybersecurity, security analysts and…
Emotet Botnet is Back!
Emotet, one of today's most prominent malware botnets, has come back to…
Microsoft July 2020 Patch Tuesday fixes 123 vulnerabilities
This month, Redmond fixed 123 security flaws across 13 products. None of…
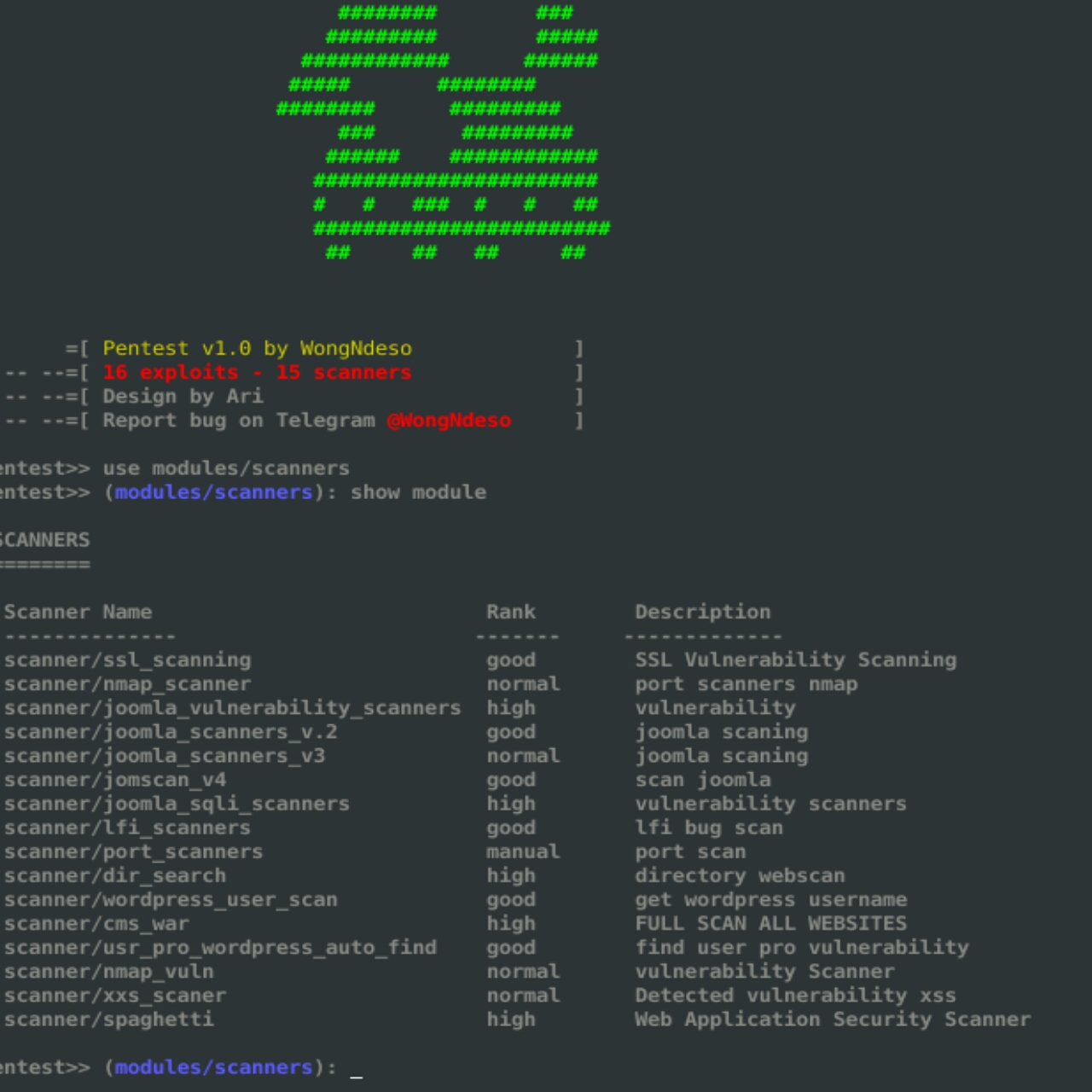
Pentest Tools Framework
Pentest Tools Framework is a database of exploits, Scanners and tools for…
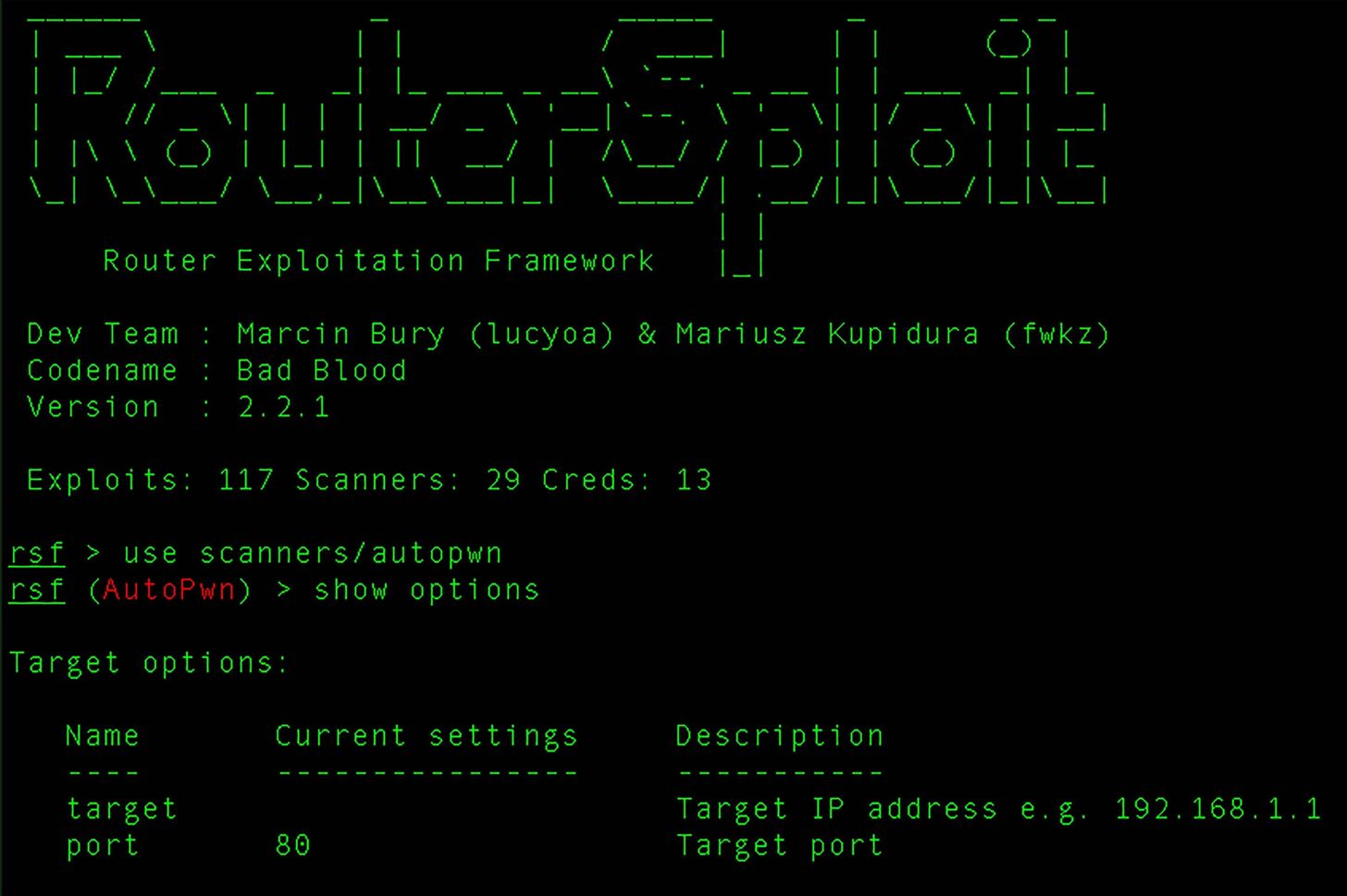
Router Exploitation Framework – RouterSploit
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices.…
Analysis of Windows Active Directory environment using BloodHound
This article examines the analysis of a Windows Active Directory environment using…
Big Data And Cyber Security
Companies are constantly looking for new ways to protect sensitive business data…
Indian IT company invaded more than 10,000 email accounts in 7 years
According to Reuters, a little-known Indian IT company provided hacking services to…